Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.

And the sum of relevant posts personnel strategies systems and procedures.
2 years ago
50
Chapter 25 information system security risk assessment 25.1 information security and information risk how to design and formulate an information security assurance system for a new system that has not yet been established?It is to analyze identify and evaluate the security risks of the information application system and formulate preventive measures for it. The relationship between information security and security risk
Loading comments...
-
 38:21
38:21
Stephen Gardner
2 days ago🔥Is Kash Patel HIDING DETAILS About Charlie Kirk & Jeffrey Epstein? Judge Joe Brown
75.9K195 -
 26:33
26:33
DeVory Darkins
1 day ago $60.77 earnedRep Omar EMBARRASSES herself in a painful way as Newsom PANICS over Kamala confrontation
108K332 -
 3:28:14
3:28:14
Badlands Media
1 day agoThe Narrative Ep. 39: The Sovereign Mind
133K39 -
 2:17:35
2:17:35
TheSaltyCracker
13 hours agoThe Charlie Kirk Effect ReeEEStream 9-21-25
149K393 -
 2:03:07
2:03:07
vivafrei
13 hours agoEp. 283: Charlie Kirk Memorial and other Stuff in the Law World
247K226 -
 9:13:12
9:13:12
The Charlie Kirk Show
23 hours agoLIVE NOW: Building A Legacy, Remembering Charlie Kirk
2.21M987 -
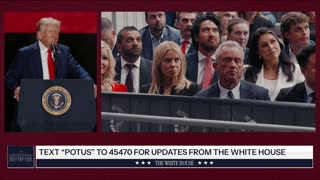 1:55:20
1:55:20
The White House
16 hours agoPresident Trump Participates in the Memorial Service for Charlie Kirk
129K97 -
 1:02:41
1:02:41
Sarah Westall
14 hours agoDomestic Terror Operation: Death Threats, Smear Campaigns, Gang Stalking w/ Journalist Sarah Fields
86K13 -
 1:51:40
1:51:40
Nerdrotic
15 hours ago $27.31 earnedGobekli Tepe Discovery and "Reconstruction" | Forbidden Frontier #118
120K15 -
 29:07
29:07
Tactical Advisor
15 hours agoATF Changes Ruling on SBR & Tacpack unboxing | Vault Room Live Stream 039
116K22