Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
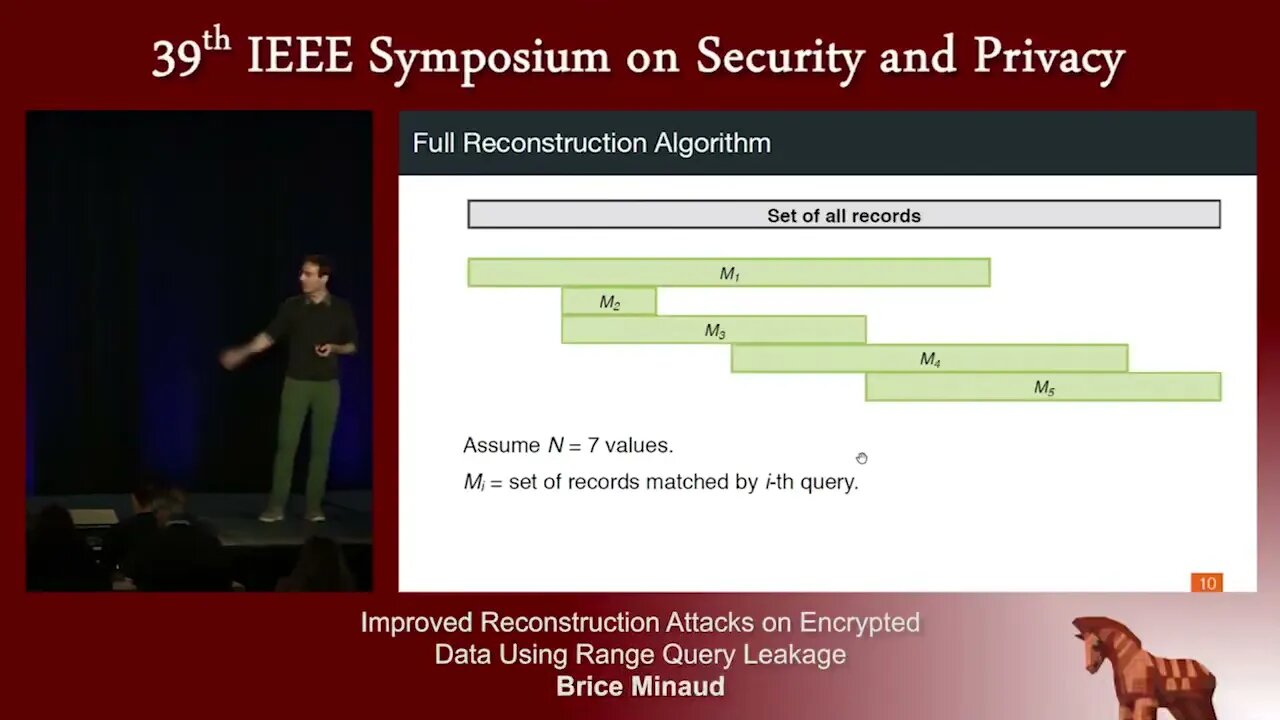
Improved Reconstruction Attacks on Encrypted Data Using Range Query Leakage
Loading comments...
-
 1:36:51
1:36:51
The Quartering
3 hours agoThe End Of Trans Madness, Alex Jones Loses Final Plea, Rock Bottom For Star Trek & More
99.1K30 -
 36:53
36:53
Stephen Gardner
2 hours ago🔥LEAKED! Trump's Secret ANTIFA Takedown Plan EXPOSED!!
15.2K15 -
 1:20:21
1:20:21
The Confessionals
4 hours agoInside the Invisible War (Demons Don't Fight Fair)
3.92K1 -
 1:07:45
1:07:45
The White House
4 hours agoPresident Trump Participates in a Bilateral Lunch with the President of the Argentine Republic
39.7K14 -
 2:13:35
2:13:35
Barry Cunningham
4 hours agoBREAKING NEWS: PRESIDENT TRUMP AND PRESIDENT OF ARGENTINA JAVIER MILEI MEET
28.8K10 -
 5:22
5:22
Michael Heaver
4 hours agoFarage Issues URGENT Warning To Britain
16.2K7 -
 1:22:01
1:22:01
Sean Unpaved
6 hours agoMNF Madness, CFB Week 7 Rewind, & MLB's ALCS & NLCS Playoff Fire!
35.9K -
 1:02:05
1:02:05
DeVory Darkins
4 hours ago $34.91 earnedTrump drops NIGHTMARE News on Democrats as the Violent protestors gear up
123K65 -
 1:59:08
1:59:08
The Charlie Kirk Show
4 hours agoCharlie’s 32nd Birthday + Medal of Freedom | Sec. Bessent, Lavorgna, Zeldin, Sen. Lee | 10.14.25
112K103 -
 LIVE
LIVE
StoneMountain64
3 hours agoBattlefield 6 Sniping and Unlocking SNIPERS from LONG RANGE
45 watching