Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
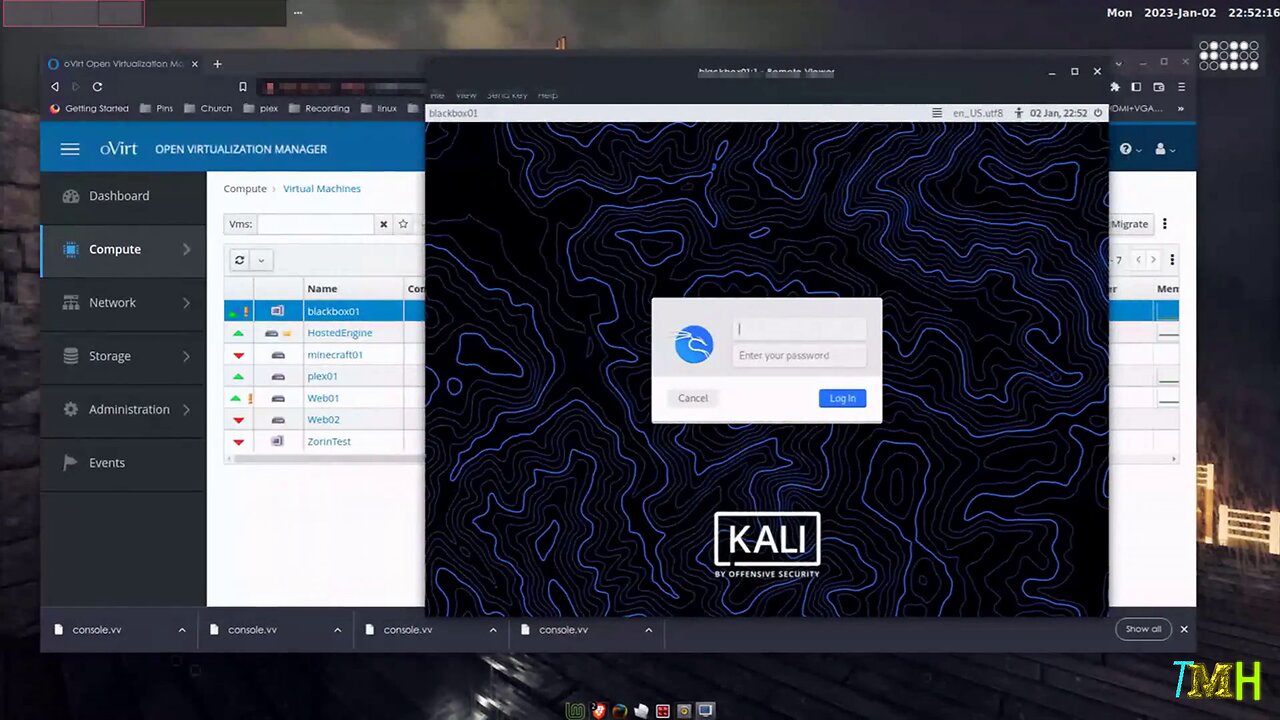
TMH - Linux - Shadow File Injection Attack
3 years ago
49
I go through how to inject the hash of a known password into the shadow file of a Kali Linux virtual machine system using a rescue image.
Loading comments...
-
 3:32:44
3:32:44
MattMorseTV
10 hours ago $30.39 earned🔴Bannon x Epstein INTERVIEW.🔴
75.1K145 -
 2:41:07
2:41:07
Tundra Tactical
8 hours ago $3.77 earned🛑🚨Dan Wesson DWX GIVEAWAY Announcement!! 🚨🛑 Tundra Tactical Recaps Shot Show 2026
35.6K -
 1:54:51
1:54:51
DLDAfterDark
9 hours ago $3.56 earnedThe Truth About Forced Reset Triggers - Rare Breed Drama & Tim Hoffman's Super Safety
37.2K7 -
 17:42
17:42
WhatCulture - Film
1 day ago $3.40 earned18 Movie Mistakes You Can Never Unsee
36.5K2 -
 4:16
4:16
RidiculousRides
1 day ago $2.71 earnedFrom Lincoln to Legend: Inside the Build of America’s Wildest Off-Road Limo
34.6K2 -
 2:50:23
2:50:23
Barry Cunningham
10 hours agoLIVE TONIGHT: There's Something BIG Going On In Fulton County And The Democrats Are FREAKING Out!
95.2K101 -
 41:34
41:34
Stephen Gardner
10 hours agoTim Walz is DONE! MN Fraud NIGHTMARE Explodes!
43.3K114 -
 9:34:37
9:34:37
Plan ₿ Forum
9 days agoPlan ₿ Forum El Salvador 2026 – Day 2 Live from the WAGMI Stage
437K18 -
 1:15:26
1:15:26
Patriots With Grit
15 hours agoCancer Breakthrough: There Is An Oasis Of Hope | Dr. Francisco Contreras
18.6K4 -
 10:00
10:00
WhatCulture Gaming
2 days ago $0.34 earned8 Video Game Endings That Were Saved By Fans
14K1