Premium Only Content

Chapter-15, LEC-2 | External Backdoor | #ethicalhacking #cybersecurity #cybersport
An external backdoor is a type of security vulnerability that allows an attacker to gain unauthorized access to a computer system or network from outside the organization. It is a hidden entry point that can be exploited by attackers to bypass normal authentication procedures and gain access to sensitive information, install malware or steal data.
Backdoors can be created by attackers who exploit known vulnerabilities in software, hardware or network devices, or by insiders who intentionally install them to gain unauthorized access to the system later. External backdoors can be particularly dangerous as they can be accessed remotely from outside the organization, often without the need for physical access to the targeted system or network.
Attackers can use various techniques to install and exploit external backdoors, such as:
Exploiting known vulnerabilities in software, hardware or network devices to gain access to the system.
Social engineering techniques, such as phishing or spear-phishing attacks, to trick users into downloading and installing malicious software.
Supply chain attacks, where attackers compromise a third-party vendor's software or hardware and use it to gain access to the target system.
Once a backdoor is installed, attackers can use it to gain persistent access to the system, even after the original vulnerability has been patched. This can allow them to steal data, modify or delete files, install additional malware, or launch attacks against other systems or networks.
To protect against external backdoors, organizations should implement strong security measures, such as regular vulnerability assessments and penetration testing, network segmentation, access controls, and employee training on security best practices. It is also important to monitor network activity and log files for signs of suspicious activity, such as unauthorized access attempts or changes to system configurations.
-
 1:30:28
1:30:28
Redacted News
3 hours agoIsrael's Government on the Verge of Collapse? Israeli's demand Netanyahu resign NOW | Redacted News
105K100 -
 1:09:29
1:09:29
vivafrei
5 hours agoRaja Jackson Charges Explained! James Comey Peads "Not Guilty"! L.A. Firest Were ARSON! & More!
108K38 -
 24:41
24:41
CharLee Simons presents DO NOT TALK
19 hours agoDINESH D'SOUZA is back on DO NOT TALK
9.98K1 -
 4:22:47
4:22:47
Right Side Broadcasting Network
9 hours agoLIVE REPLAY: President Trump Participates in a Roundtable on ANTIFA - 10/8/25
106K97 -
 LIVE
LIVE
Dr Disrespect
8 hours ago🔴LIVE - DR DISRESPECT - BLACK OPS 7 - BANG BANG BANG
1,133 watching -
 1:35:05
1:35:05
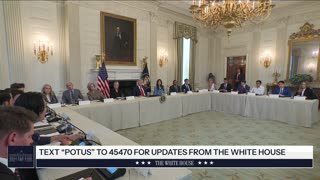
The White House
5 hours agoPresident Trump Participates in a Roundtable on ANTIFA
41.8K49 -
 LIVE
LIVE
LFA TV
20 hours agoLIVE & BREAKING NEWS! | WEDNESDAY 10/8/25
831 watching -
 3:33:37
3:33:37
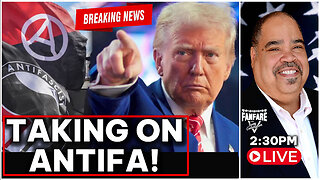
Barry Cunningham
7 hours agoBREAKING NEWS: PRESIDENT TRUMP HOSTS ROUNDTABLE DISCUSSION ABOUT ANTIFA!
37.7K17 -
 20:03
20:03
ThinkStory
9 hours agoGEN V Season 2 Episode 6 Breakdown! Cipher's Power, Stan's Plan & Polarity Explained!
11.1K -
 2:19:38
2:19:38
The Robert Scott Bell Show
8 hours agoTom Renz, Medical Kidnapping, Trust in Doctors Declines, Allergy-Suicide Link, Rockefeller’s Food Agenda - The RSB Show 10-8-25
20.6K6
