Premium Only Content
Chapter-17, LEC-4 | Downloading Files | #ethicalhacking #cybersport #cybersecurity
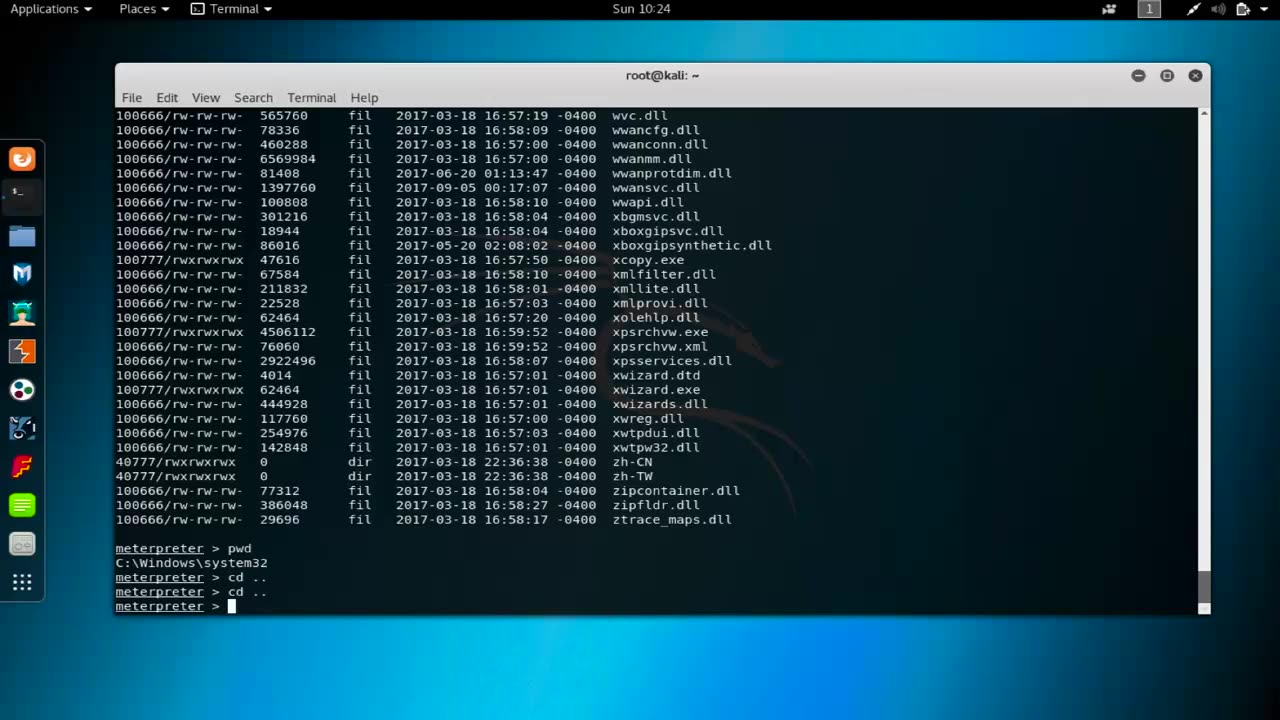
Downloading files is a common post-hacking session technique that is used to extract sensitive data or other valuable information from a compromised system or network. This technique is often used by attackers to exfiltrate stolen data or to download additional tools or payloads onto the compromised system.
When an attacker gains access to a system using a Meterpreter payload or other post-exploitation tool, they can use various techniques to download files from the compromised system. For example, they can use the "download" command in Meterpreter to transfer specific files or folders to the attacker's machine. Alternatively, they can use other tools, such as FTP or SCP, to copy files to a remote server or cloud storage service.
Downloading files can be a time-consuming process, especially if the target system contains large amounts of data. To speed up the process, attackers may use compression tools like "tar" or "zip" to bundle multiple files or folders together and transfer them in a single archive. They may also use network-level techniques like port-forwarding or VPNs to bypass firewalls or other security measures that may block the transfer of files.
Downloading files can be a risky post-hacking session technique because it leaves traces of the attacker's activities on the compromised system, making it easier for security teams to detect and investigate the breach. As such, attackers may use various tactics to obfuscate their activities, such as deleting logs or using encryption to hide the data that is being exfiltrated.
Overall, downloading files is a powerful post-hacking session technique that can allow attackers to exfiltrate sensitive data or download additional tools or payloads onto the compromised system. However, it is also a high-risk technique that requires careful planning and execution to avoid detection and ensure a successful breach.
-
 LIVE
LIVE
SpartakusLIVE
5 hours agoBattlefield 6 - REDSEC || ARC Raiders Later? || Anybody Want Warzone???
621 watching -
 LIVE
LIVE
Alex Zedra
1 hour agoLIVE! Spooky Games tn
183 watching -
 LIVE
LIVE
I_Came_With_Fire_Podcast
12 hours agoThe Normalization of Political Violence | Right Wing In-Fighting | China Chooses China
152 watching -
 LIVE
LIVE
PandaSub2000
7 hours agoLIVE 10:30pm ET | BUZZ TRIVIA with Chat!
115 watching -
 LIVE
LIVE
ThisIsDeLaCruz
1 hour agoWhat Fans Never Hear: Pearl Jam’s Audio Engineer Tells His Story
84 watching -
 1:39:58
1:39:58
Glenn Greenwald
4 hours agoWhy Did Zohran Win & What Does it Mean? Plus: Dick Cheney, "Hero of the Resistance" | SYSTEM UPDATE #543
113K62 -
 LIVE
LIVE
This is the Ray Gaming
1 hour agoRAYmember RAYmember the 5th of November | Rumble Premium Creator
61 watching -
 1:44:39
1:44:39
vivafrei
4 hours agoArctic Frost is Bigger Scandal than you Think!! Live with Former Green Beret Ivan Raiklin!
48.6K39 -
 2:29:57
2:29:57
Turning Point USA
3 hours agoTPUSA Presents This Is the Turning Point Tour LIVE with Eric and Lara Trump at Auburn University!
46.5K11 -

XDDX_HiTower
2 hours agoBATTLEFIELD 6 REDSEC! [RGMT CONTENT Mgr.
5.33K1