Premium Only Content
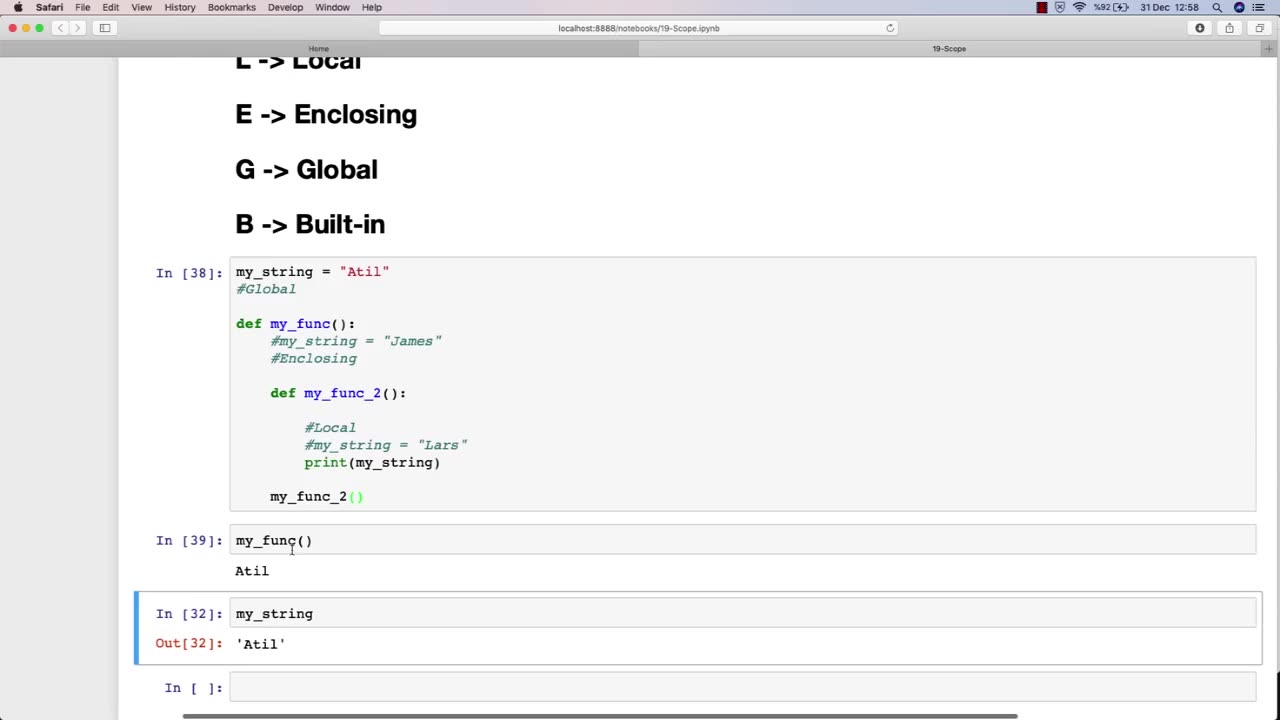
Chapter-30, LEC-6 | SCOPE | #ethicalhacking #education #hacking #rumble
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy
The scope of an ethical hacking course is vast and covers a wide range of topics related to cybersecurity and information security. At a high level, the scope of an ethical hacking course typically includes:
Understanding the fundamentals of cybersecurity: This includes understanding the various types of cybersecurity threats, such as viruses, malware, and phishing attacks, and the principles of risk management and threat modeling.
Network security: This includes understanding the fundamentals of network architecture and protocols, as well as how to secure networks against attacks such as denial-of-service (DoS) attacks and man-in-the-middle (MITM) attacks.
Web application security: This includes understanding the principles of web application architecture and how to secure web applications against common attacks such as cross-site scripting (XSS) and SQL injection.
Wireless security: This includes understanding the fundamentals of wireless networks and how to secure them against attacks such as rogue access points and eavesdropping.
Penetration testing: This includes understanding the principles of penetration testing and how to conduct effective ethical hacking activities, including reconnaissance, vulnerability assessment, and exploitation.
Ethical and legal considerations: This includes understanding the ethical and legal considerations associated with ethical hacking, such as obtaining permission and respecting privacy.
The scope of an ethical hacking course is constantly evolving to keep pace with the ever-changing cybersecurity landscape. As new threats emerge and new technologies are developed, the scope of an ethical hacking course must adapt to provide students with the latest knowledge and techniques in the field of cybersecurity.
-
 LIVE
LIVE
The Charlie Kirk Show
43 minutes agoThe Killer AG + Kav Assassin's 8 Years + The Battle of Portland | Hemingway, Davis | 10.6.2025
6,276 watching -
 LIVE
LIVE
Right Side Broadcasting Network
3 hours agoLIVE: White House Press Secretary Karoline Leavitt Holds a Press Briefing - 10/6/25
2,363 watching -
 LIVE
LIVE
Steven Crowder
3 hours ago🔴 Deport Them All: Trump Takes Fight to Leftist Chicago & Portland Over Attacks on ICE
26,031 watching -
 1:01:46
1:01:46
The Rubin Report
1 hour agoBill Maher’s Crowd Stunned as Van Jones Gives a Brutal Message to Liberal Media
23.8K36 -
 LIVE
LIVE
Nerdrotic
2 hours agoHollywood Will EAT Itself | Amazon BENDS The Knee to 007 Fans - Nerdrotic Nooner 524
351 watching -
 LIVE
LIVE
The Shannon Joy Show
2 hours agoMoody’s: Recession Incoming! Economic Slowdown Crushing Americans while Trump builds a ballroom
199 watching -
 LIVE
LIVE
The Mel K Show
1 hour agoMORNINGS WITH MEL K -Armor of God: Humanity Must Choose their Destiny 10-6-25
691 watching -
 LIVE
LIVE
LFA TV
17 hours agoLIVE & BREAKING NEWS! | MONDAY 10/6/25
4,092 watching -
 LIVE
LIVE
Trumpet Daily
1 hour agoTrumpet Daily LIVE | October 6, 2025
313 watching -
 30:03
30:03
Tudor Dixon
2 hours agoRep. Tim Burchett on the Government Shutdown & Leadership Crisis | The Tudor Dixon Podcast
2.49K
