Premium Only Content
Chapter-35, LEC-2 | MITM Refreshed | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
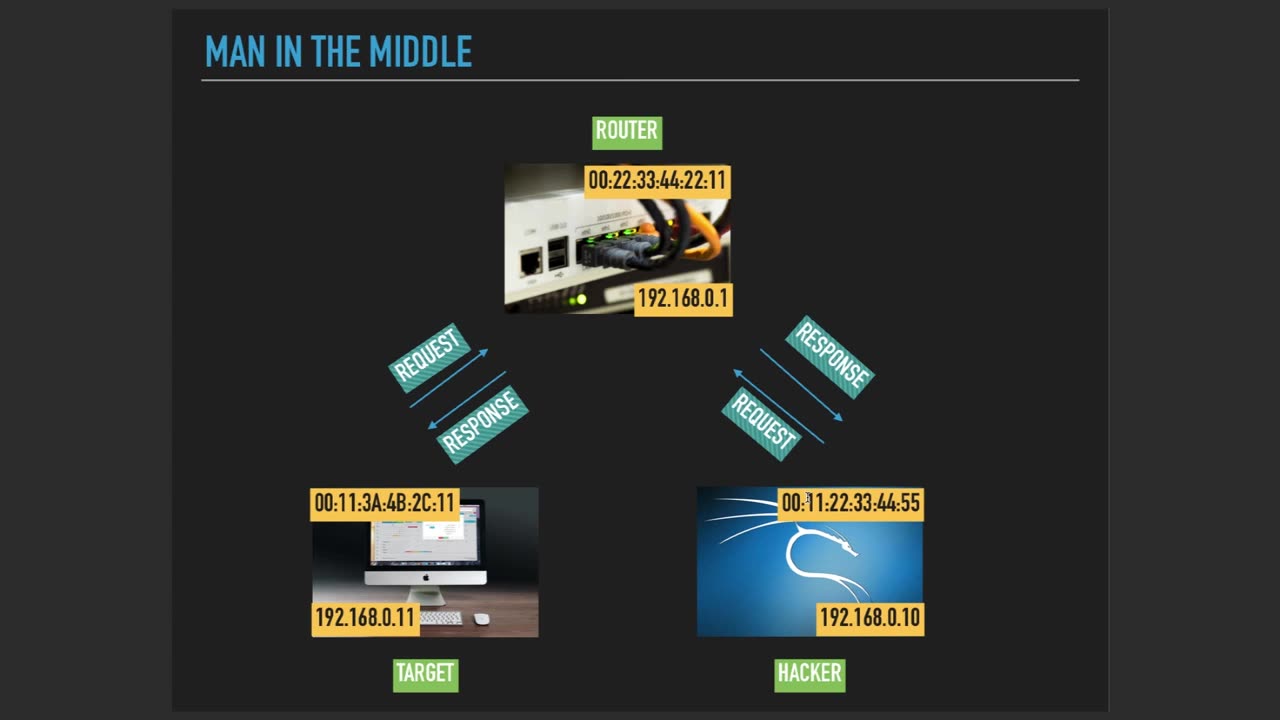
MITM Refreshed is a modern and sophisticated variation of the traditional Man-in-the-Middle (MITM) attack, which is a type of cyber attack that intercepts communication between two parties. In a MITM Refreshed attack, the attacker employs advanced techniques and tools to circumvent modern security measures and gain unauthorized access to sensitive information.
Unlike traditional MITM attacks, which may rely on known vulnerabilities or basic spoofing techniques, MITM Refreshed attacks often utilize sophisticated methods, such as zero-day exploits, advanced social engineering, or complex malware, to intercept and manipulate communication. This makes them highly effective and challenging to detect.
In a MITM Refreshed attack, the attacker may target various communication channels, including wired or wireless networks, web applications, email systems, or even encrypted connections. By positioning themselves between the legitimate parties, the attacker can stealthily monitor, modify, or inject malicious data into the communication without raising suspicion.
The consequences of a MITM Refreshed attack can be severe, as it can lead to data breaches, financial loss, reputational damage, and legal repercussions. Organizations and individuals must employ robust security measures, such as multi-factor authentication, encryption, intrusion detection systems, and regular security audits, to defend against MITM Refreshed attacks. Ongoing training and awareness programs to educate users about the risks and best practices for securely communicating and transmitting sensitive information are also critical in mitigating the threat of MITM Refreshed attacks.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
TimcastIRL
1 hour agoLEAKED Memo Says NO BACK PAY For Federal Workers Amid Government Shutdown | Timcast IRL
27,302 watching -
 LIVE
LIVE
Turning Point USA
53 minutes agoTPUSA Presents This is The Turning Point Tour LIVE with Vivek Ramaswamy!
841 watching -
 LIVE
LIVE
Barry Cunningham
1 hour agoPRESIDENT TRUMP IS BRINGING THE RECKONING TO THE DEEP STATE!
2,128 watching -
 LIVE
LIVE
Sarah Westall
2 hours agoSuperhuman Hearing of the Matrix: Reality is Different w/ Sharry Edwards
171 watching -
 LIVE
LIVE
LFA TV
23 hours agoLIVE & BREAKING NEWS! | TUESDAY 10/7/25
609 watching -
 DVR
DVR
Stephen Gardner
51 minutes ago🔥BOMBSHELL: Trump's NEW REPORT Catches Democrats Red-Handed!
3 -
 10:20
10:20
Ken LaCorte: Elephants in Rooms
6 hours agoWhen does a fetus become a baby?
312 -
 1:40:39
1:40:39
Glenn Greenwald
5 hours agoPam Bondi's Malicious Ineptitude on Full Display During Senate Hearing; Pro-Spying Senators Complain About Being Surveilled; What New Candace/Charlie Kirk Messages Reveal | SYSTEM UPDATE #528
88.3K81 -
 LIVE
LIVE
SpartakusLIVE
2 hours agoPREPARE to have your Frontal Lobe SEARED with MIND BENDING Content
218 watching -
 LIVE
LIVE
Nikko Ortiz
1 hour agoRealistic COP Simulator | Rumble LIVE
98 watching
