Premium Only Content
Chapter-35, LEC-2 | MITM Refreshed | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
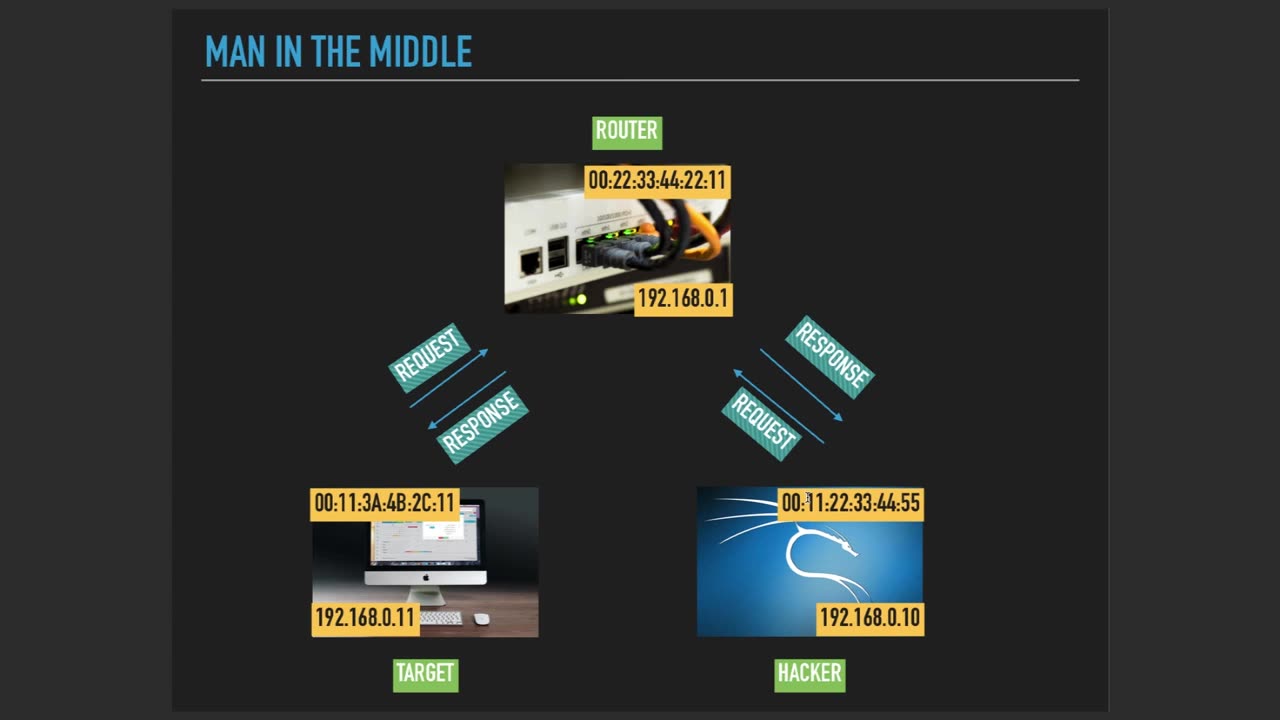
MITM Refreshed is a modern and sophisticated variation of the traditional Man-in-the-Middle (MITM) attack, which is a type of cyber attack that intercepts communication between two parties. In a MITM Refreshed attack, the attacker employs advanced techniques and tools to circumvent modern security measures and gain unauthorized access to sensitive information.
Unlike traditional MITM attacks, which may rely on known vulnerabilities or basic spoofing techniques, MITM Refreshed attacks often utilize sophisticated methods, such as zero-day exploits, advanced social engineering, or complex malware, to intercept and manipulate communication. This makes them highly effective and challenging to detect.
In a MITM Refreshed attack, the attacker may target various communication channels, including wired or wireless networks, web applications, email systems, or even encrypted connections. By positioning themselves between the legitimate parties, the attacker can stealthily monitor, modify, or inject malicious data into the communication without raising suspicion.
The consequences of a MITM Refreshed attack can be severe, as it can lead to data breaches, financial loss, reputational damage, and legal repercussions. Organizations and individuals must employ robust security measures, such as multi-factor authentication, encryption, intrusion detection systems, and regular security audits, to defend against MITM Refreshed attacks. Ongoing training and awareness programs to educate users about the risks and best practices for securely communicating and transmitting sensitive information are also critical in mitigating the threat of MITM Refreshed attacks.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-

FreshandFit
12 hours agoHow Difficult Is It For Men In Dating Apps? Girls Find Out...
140K22 -
 1:57:58
1:57:58
Badlands Media
7 hours agoBaseless Conspiracies Ep. 152: Government Shutdown Games & The Kirk Assassination Theories
62.6K4 -
 2:02:42
2:02:42
Inverted World Live
5 hours agoTrump's Medbeds | Ep. 115
73K9 -
 2:03:41
2:03:41
TimcastIRL
6 hours agoTrump To Deploy National Guard To Chicago, Federal TAKEOVER Begins | Timcast IRL
211K176 -
 2:52:40
2:52:40
PandaSub2000
11 hours agoLIVE 10pm ET | SILENT HILL F w/TinyPandaFace
32.1K1 -
 1:26:00
1:26:00
Glenn Greenwald
12 hours agoNick Fuentes On Censorship, Charlie Kirk's Assassination, Trump's Foreign Policy, Israel/Gaza, the Future of the GOP, and More | SYSTEM UPDATE #523
131K339 -
 5:49:04
5:49:04
StevieTLIVE
8 hours ago#1 Kar98 Warzone POV Monday MOTIVATION
26.3K1 -
 4:45:45
4:45:45
a12cat34dog
7 hours agoTHE *NEW* SILENT HILL :: SILENT HILL f :: IS IT GOOD!? {18+}
22K4 -
 1:00:21
1:00:21
Akademiks
5 hours agonba youngboy live show.
56.8K2 -
 2:51:15
2:51:15
The Quartering
5 hours agoThey Just Stopped Another Attack, Trump Defeats Youtube, Hasan PIker Meltdown & More
69.1K49