Premium Only Content
Chapter-36, LEC-7 | Protecting Overselves | #ethicalhacking #hacking
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
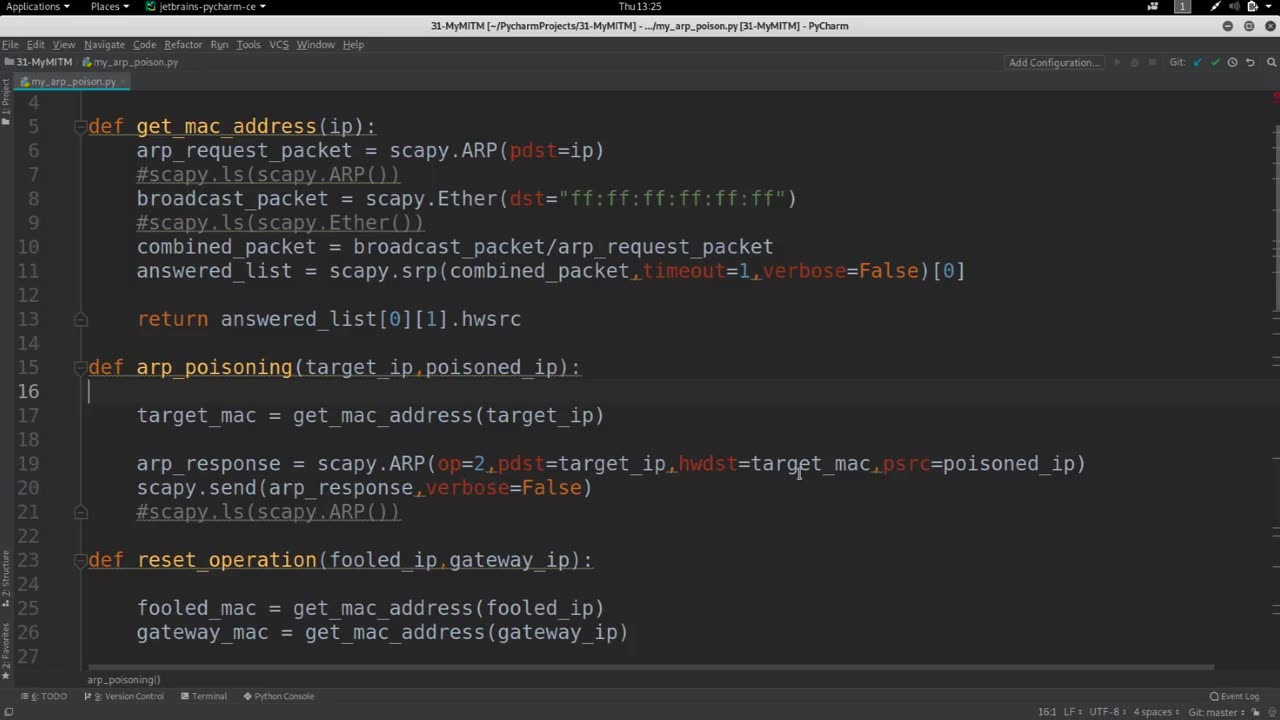
Protecting ourselves refers to taking measures and precautions to safeguard our personal information, privacy, and security in various aspects of our lives, including online activities, physical security, and data protection. With the increasing prevalence of digital technologies and the internet, protecting ourselves has become crucial to prevent potential risks and threats, such as identity theft, data breaches, cyber attacks, physical harm, and financial loss.
Protecting ourselves involves adopting good security practices and being vigilant in our daily activities. This can include:
Securing online accounts: Using strong and unique passwords for each online account, enabling two-factor authentication (2FA), and being cautious of phishing attempts and social engineering attacks to prevent unauthorized access to our online accounts.
Being mindful of personal information: Being cautious about sharing personal information online, including on social media, and being aware of the privacy settings and permissions of the apps and platforms we use.
Keeping devices and software updated: Regularly updating our operating systems, apps, and software with the latest security patches and fixes to protect against known vulnerabilities.
Using encryption and secure communication: Using encryption technologies, such as HTTPS for websites, and virtual private networks (VPNs) for secure communications, especially when accessing sensitive information or using public Wi-Fi networks.
Being cautious with emails and attachments: Avoiding opening suspicious emails or attachments, and being cautious of phishing emails or emails from unknown sources that may contain malware or viruses.
Protecting physical security: Locking our doors and windows, using security systems and surveillance cameras, and being cautious with strangers or suspicious activities in our physical surroundings.
Being mindful of social media and online presence: Being cautious about the information we share on social media, being mindful of our online presence, and adjusting privacy settings to control what information is visible to others.
Backing up important data: Regularly backing up important files and data to prevent loss due to data breaches, hardware failure, or other unforeseen events.
Educating ourselves about cybersecurity: Staying informed about the latest cybersecurity threats, trends, and best practices through reliable sources, and educating ourselves and our family members about safe online practices.
Protecting ourselves requires a proactive approach, constant vigilance, and staying informed about the evolving landscape of cybersecurity threats. By taking steps to protect our personal information, privacy, and security, we can minimize the risks of becoming victims of cybercrime and other security breaches.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 52:56
52:56
X22 Report
2 hours agoMr & Mrs X - Halftime Narrative Failed, Epstein Is A Puppet, Trump Is Saving America - EP 26
22K14 -
 24:09
24:09
The Rubin Report
3 hours agoHow Dems Created an ICE Recipe for Disaster on Purpose | Anna Paulina Luna
7.75K20 -
 20:02
20:02
WhatCulture - Film
3 days ago20 Movie Reveals Nobody Noticed
351 -
 6:49
6:49
RidiculousRides
21 hours agoPeel P50: The 59kg Car You Can Park Indoors
7393 -
 13:02
13:02
WhatCulture Gaming
1 day ago10 Video Games That Broke The Rules
460 -
 2:12:02
2:12:02
Battlefront: Frontline with Dustin Faulkner
12 hours agoThe DoJ Leadership Reveals Failure to the People with Epstein Files During Bondi Testimony | Has the GOP Lost the Midterms with Bad Focus | Trust in Media and Government Definitely Failing in the West
1.06K1 -
 7:58
7:58
CinemaBlend
1 day ago'The Penguin' Interviews With Colin Farrell, Cristin Milioti, Matt Reeves And More
391 -
 22:33
22:33
Welker Farms
1 day ago $6.49 earned$4,000 Leak? Let's Crack It Open & Investigate!
54.1K9 -
 20:42
20:42
Jasmin Laine
16 hours agoSupreme Court CANCELS Election Win—Liberal MP LOSES It After VIRAL Clip HAUNTS Him
32.1K55 -
 15:03
15:03
tactical_rifleman
23 hours ago $6.81 earnedGriffin Armament MK2 Review
23.3K7