Premium Only Content
Chapter-38, LEC-4 | Running Commands | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
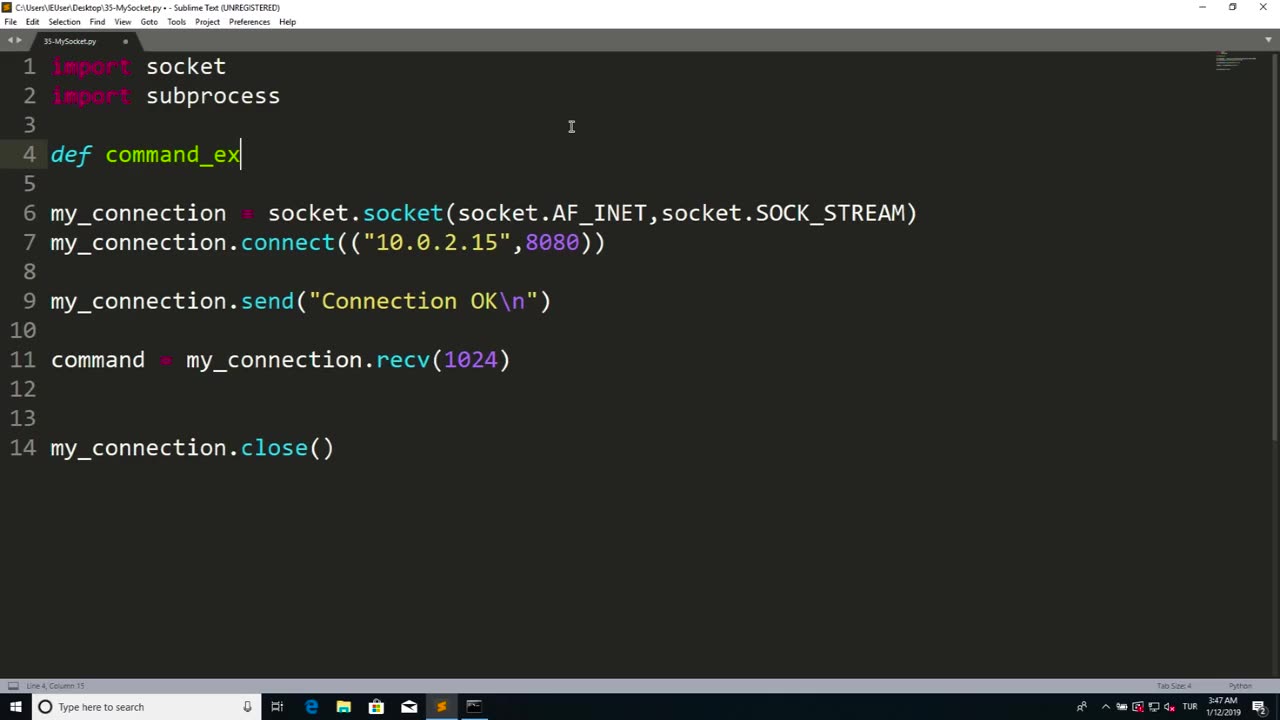
Running commands refers to the process of executing instructions or commands in a computer system or software to perform specific tasks or operations. Commands are typically entered into a command-line interface or terminal, which allows users to interact with a computer system directly through text-based commands.
Running commands can be used for a wide range of purposes, including system administration, software configuration, troubleshooting, automation, and more. Commands can be used to manipulate files and directories, configure settings, install or uninstall software, manage processes, retrieve information, and perform other operations depending on the specific software or system being used.
Running commands requires knowledge of the specific command syntax, options, and parameters for the software or system being used. It is important to understand the implications and potential consequences of the commands being executed, as they can impact the performance, stability, and security of the system or software.
Proper caution and authorization must be exercised when running commands, as some commands may have elevated privileges and can potentially cause harm or damage to the system or data if used improperly or without proper authorization. It is essential to follow best practices, such as using appropriate permissions, verifying the source and integrity of commands, and testing commands in a safe and controlled environment.
Running commands can be a powerful tool in managing computer systems and software efficiently and effectively. However, it requires knowledge, expertise, and responsible use to ensure that commands are executed safely and securely, and that the intended tasks or operations are performed accurately and without any unintended consequences. Always exercise caution, follow proper authorization procedures, and adhere to best practices when running commands in any computer system or software environment.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 4:26
4:26
GreenMan Studio
1 day agoGREENMANS STOCKING STUFFERS 5 – GREENMAN AI
14.9K5 -
 5:00
5:00
SethDrums
4 days ago $8.42 earnedStaind – It's Been Awhile if it was 1980s
76.8K18 -
 20:18
20:18
itsSeanDaniel
2 days agoCandace Owens CALLED OUT by Piers Morgan, So She FIRES BACK
23.2K22 -
 4:57:14
4:57:14
Akademiks
14 hours ago21 Savage Wants Young Thug, Wham & Gunna to SQUASH IT! Future Sneak Dissing? Jim Jones Pays 50 Cent?
406K13 -
 6:01:38
6:01:38
Right Side Broadcasting Network
2 days agoLIVE: President Trump to Deliver Remarks in Rocky Mount, NC - 12/19/25
160K65 -
 3:24:48
3:24:48
VapinGamers
13 hours ago $50.36 earnedDestiny 2 - Dungeons and Loot with Friends - !rumbot !music
122K1 -
 2:07:44
2:07:44
TimcastIRL
13 hours agoTrump's Secret Plan To Make Charlie Kirk VP, America Fest IN CIVIL WAR | Timcast IRL
253K260 -
 4:09:13
4:09:13
I_Came_With_Fire_Podcast
22 hours agoLive Fire: Christmas Special
62.4K19 -
 46:26
46:26
Sarah Westall
16 hours agoWhat’s Behind the Silver Surge? Large Institutions Cashing In w/ Andy Schectman
56.9K4 -
 6:42:10
6:42:10
Turning Point USA
21 hours agoLIVE NOW: AMFEST DAY 2 - VIVEK, JACK POSOBIEC, MEGYN KELLY, ALEX CLARK AND MORE…
1.46M205