Premium Only Content
Chapter-38, LEC-13 | Getting Contents | #ethicalhacking #content #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
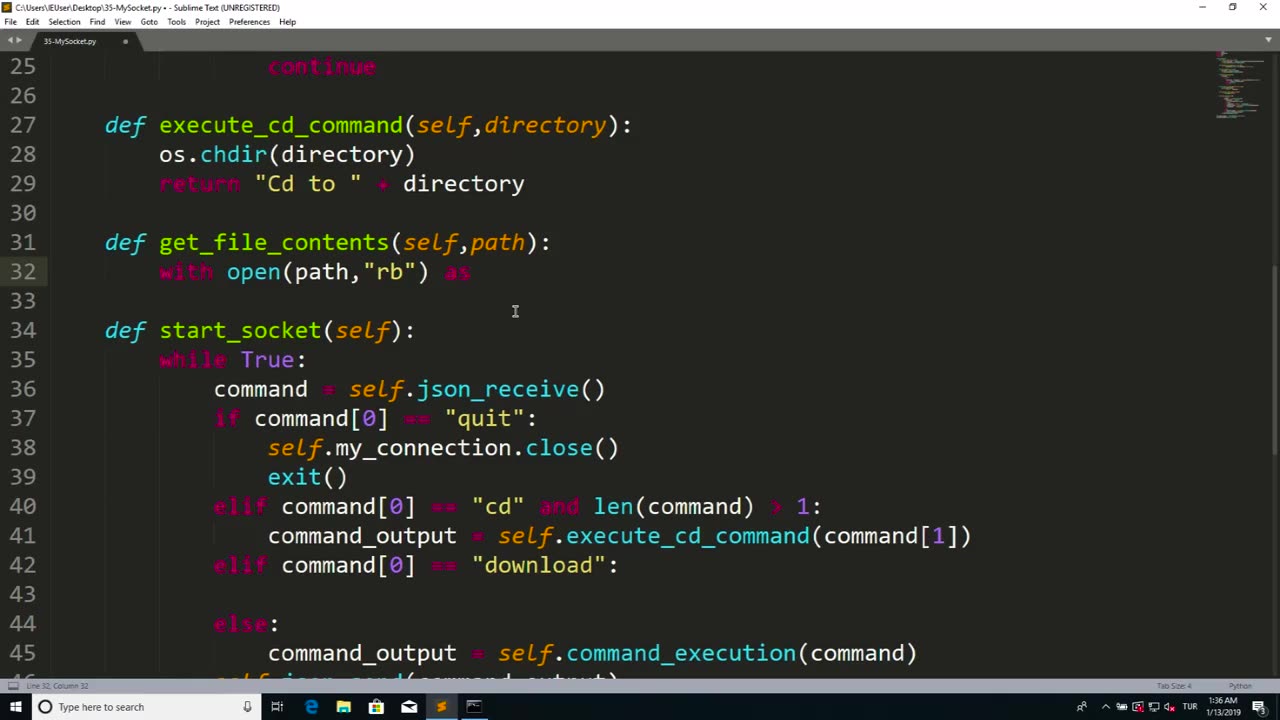
"Getting Contents" is a general term that refers to the process of retrieving data or information from a source, such as a file, a database, a web page, or an API. The implementation of "Getting Contents" may vary depending on the specific source or technology being used.
Here's a general description of how "Getting Contents" can be implemented:
Identifying the source: The first step in getting contents is identifying the source from which the data or information needs to be retrieved. This may involve specifying the file path, the database connection details, the URL of a web page, or the endpoint of an API.
Establishing a connection: Once the source is identified, the implementation of "Getting Contents" may involve establishing a connection to the source. This may involve opening a file, establishing a database connection, making an HTTP request to a web page, or creating a connection to an API.
Retrieving data: After establishing a connection, the implementation of "Getting Contents" typically involves retrieving the data or information from the source. This may involve reading the contents of a file, executing queries to retrieve data from a database, making GET requests to retrieve data from a web page, or calling API endpoints to fetch data.
Parsing or processing data: Once the data is retrieved, the implementation of "Getting Contents" may involve parsing or processing the data to extract the relevant information or transform it into a desired format. This may involve parsing JSON, XML, CSV, or other data formats, extracting data from HTML pages, or processing data from APIs.
Handling errors and exceptions: The implementation of "Getting Contents" should include proper error handling and exception management to handle cases where the data retrieval process fails due to various reasons, such as invalid source, network errors, authentication issues, or data format errors. This may involve checking for error codes, handling exceptions, and providing appropriate error messages or fallback mechanisms.
Closing connections: Once the data retrieval process is complete, the implementation of "Getting Contents" may involve closing the connections or releasing any resources that were acquired during the process, such as closing files, closing database connections, or releasing network resources.
Using retrieved data: Finally, the retrieved data can be used for further processing, analysis, display, or other purposes as needed by the specific use case or application.
The implementation of "Getting Contents" can vary greatly depending on the source, technology, and specific requirements of the task. It may involve various steps such as identifying the source, establishing connections, retrieving data, parsing or processing data, handling errors, and using the retrieved data for further purposes. Proper implementation should include error handling, resource management, and adherence to relevant coding standards or best practices to ensure efficient and reliable functionality.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 33:59
33:59
ComedyDynamics
23 days agoBest of Jim Breuer: Let's Clear the Air
19K9 -
 2:11:03
2:11:03
Badlands Media
23 hours agoDevolution Power Hour Ep. 391: First Principles, Psyops, and Hybrid Warfare
84.4K71 -
 2:45:52
2:45:52
BlackDiamondGunsandGear
9 hours agoAfter Hours Armory / America After Charlie Kirk
34.7K12 -
 2:08:04
2:08:04
Tundra Tactical
7 hours ago $21.48 earned🎉 Pro-2A Party LIVE! | Gun Games, Freedom Vibes & Letting Loose 🔫🇺🇸
56.8K3 -
 5:21:52
5:21:52
Rallied
7 hours ago $3.56 earnedWarzone Challenges All Night
31.2K2 -
 2:45:52
2:45:52
DLDAfterDark
8 hours ago $12.50 earnedWhat Are We Missing From The Charlie Kirk Incident? Feat. TN Tactical - After Hours Armory Live!
36.5K8 -
 16:23
16:23
True Crime | Unsolved Cases | Mysterious Stories
1 month ago $4.81 earnedThe Strange Disappearance of Mekayla Bali | (Mini-Documentary)
32.9K5 -
 10:03
10:03
nospeedlimitgermany
13 days ago $8.15 earnedVW Golf 5 R32 | 250 PS | Top Speed Drive German Autobahn No Speed Limit POV
36.4K6 -
 1:35
1:35
Memology 101
1 day ago $6.09 earnedChicago Mayor Johnson calls LAW ENFORCEMENT a "SICKNESS" he will "ERADICATE"
35.9K41 -
 10:17
10:17
Advanced Level Diagnostics
13 days ago $6.63 earned2007 Chevy Express - Replaced Everything But The Code Remains!
40.4K