Premium Only Content
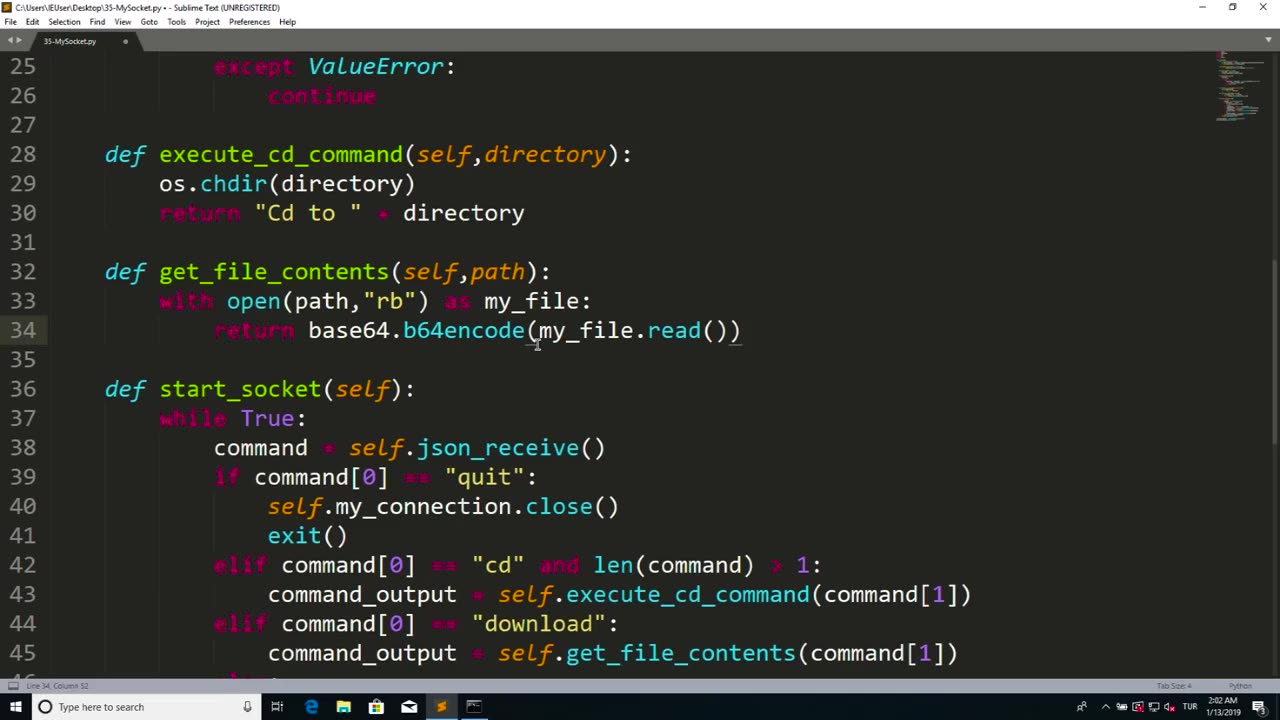
Chapter-38, LEC-15 | Encoding Downloads | #ethicalhacking #hacking #encoding #downloads
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
"Encoding Downloads" refers to the process of converting data into a specific encoding format before downloading it from the internet. This process involves transforming data into a format that is suitable for transmission over networks or storage in a specific file format, ensuring that the data can be correctly interpreted and used by the recipient.
Here's a general description of how "Encoding Downloads" can be implemented:
Identifying the data to be downloaded: The first step in the "Encoding Downloads" process is identifying the data that needs to be downloaded. This may include files, media, or other types of data that are available for download from a website, server, or other online source.
Determining the appropriate encoding format: Depending on the type of data being downloaded and the intended use, the appropriate encoding format needs to be determined. Common encoding formats include ASCII, UTF-8, Base64, binary, hexadecimal, and others. The choice of encoding format may depend on factors such as the type of data, the desired file size, the compatibility with the recipient's system, and other requirements.
Encoding the data: Once the appropriate encoding format is determined, the data needs to be encoded using the selected format. This may involve using encoding libraries or functions in the programming language being used, or specialized encoding tools or algorithms.
Adding encoding metadata: In some cases, it may be necessary to add metadata or additional information about the encoding format or the encoded data. For example, if the data is being encoded in Base64 format, metadata may need to be added to indicate that it is a Base64-encoded file. This metadata can be used by the recipient to correctly decode the data.
Preparing the encoded data for download: After the data is encoded, it needs to be prepared for download. This may involve packaging the encoded data into a specific file format, such as a ZIP archive, or generating a download link or URL that points to the encoded data.
Handling errors and exceptions: The implementation of "Encoding Downloads" should include proper error handling and exception management to handle cases where the encoding process fails due to various reasons, such as invalid data, unsupported encoding format, or other errors. This may involve checking for error codes, handling exceptions, and providing appropriate error messages or fallback mechanisms.
Initiating the download: Once the data is encoded and prepared for download, the download process can be initiated. This may involve providing a download link or URL to the recipient, triggering a download request, or performing other necessary steps to initiate the download process.
The implementation of "Encoding Downloads" can vary depending on the programming language, platform, and specific requirements of the task. It may involve steps such as identifying the data to be downloaded, determining the appropriate encoding format, encoding the data, adding encoding metadata, preparing the encoded data for download, handling errors, and initiating the download process. Proper implementation should ensure that the encoded data is accurately prepared for download and can be correctly decoded by the recipient to obtain the original data.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 4:57:14
4:57:14
Akademiks
9 hours ago21 Savage Wants Young Thug, Wham & Gunna to SQUASH IT! Future Sneak Dissing? Jim Jones Pays 50 Cent?
344K8 -
 6:01:38
6:01:38
Right Side Broadcasting Network
2 days agoLIVE: President Trump to Deliver Remarks in Rocky Mount, NC - 12/19/25
135K57 -
 3:24:48
3:24:48
VapinGamers
8 hours ago $32.47 earnedDestiny 2 - Dungeons and Loot with Friends - !rumbot !music
96.7K1 -
 2:07:44
2:07:44
TimcastIRL
9 hours agoTrump's Secret Plan To Make Charlie Kirk VP, America Fest IN CIVIL WAR | Timcast IRL
223K198 -
 4:09:13
4:09:13
I_Came_With_Fire_Podcast
17 hours agoLive Fire: Christmas Special
44K8 -
 46:26
46:26
Sarah Westall
11 hours agoWhat’s Behind the Silver Surge? Large Institutions Cashing In w/ Andy Schectman
44.1K3 -
 6:42:10
6:42:10
Turning Point USA
16 hours agoLIVE NOW: AMFEST DAY 2 - VIVEK, JACK POSOBIEC, MEGYN KELLY, ALEX CLARK AND MORE…
1.3M188 -
 1:14:37
1:14:37
Flyover Conservatives
1 day agoHow to Win 2026 Before It Starts — Clay Clark’s Goal-Setting Blueprint | FOC Show
43.9K1 -
 12:52
12:52
The Kevin Trudeau Show Limitless
2 days agoBeyond Good And Bad: The Hidden Reality Code
90.4K21 -
 1:03:11
1:03:11
BonginoReport
12 hours agoBrown U Security Failures EXPOSED - Nightly Scroll w/ Hayley Caronia (Ep.201)
164K49