Premium Only Content
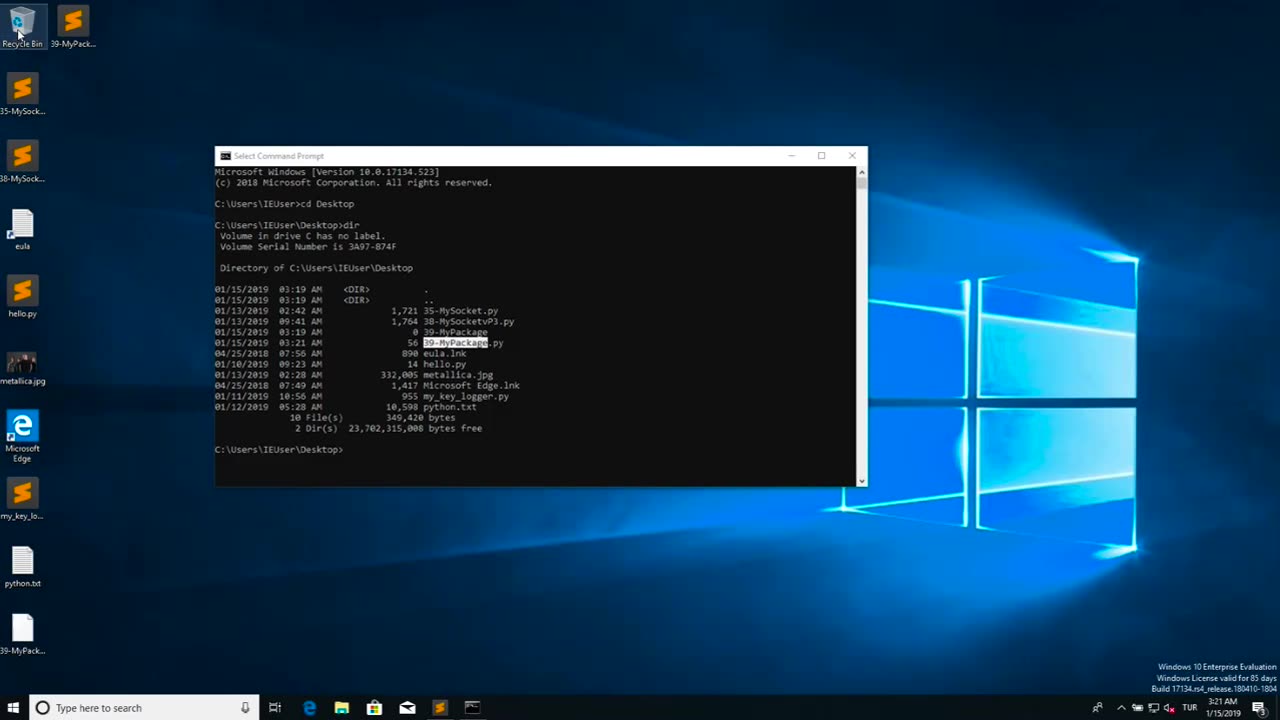
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Game On!
15 hours agoIs This The Start of a DYNASTY For The Seattle Seahawks?
345 watching -
 LIVE
LIVE
Chad Prather
13 hours agoLust, Love, and the Radical Ways of Jesus: Matthew 5:27-48 Explained
4,123 watching -
 12:05
12:05
VSOGunChannel
17 hours ago $0.26 earnedCalifornia Attacks the Internet & 3D Printing
2.6K2 -
 LIVE
LIVE
BEK TV
22 hours agoTrent Loos in the Morning - 2/10/2026
324 watching -
 11:17
11:17
Actual Justice Warrior
13 hours agoBlack Restaurant Gets ROBBED Immediately After Opening
50.7K27 -
 34:09
34:09
ZeeeMedia
15 hours agoEpstein Death Statement Drafted Day Before His 'Death' | Daily Pulse Ep 193
22.4K12 -
 2:01:22
2:01:22
MG Show
19 hours agoEpstein Files Explode: Bannon, Byrne, Flynn & Powell Epstein Ties Exposed; Deep State in Panic?
29.3K35 -
 9:02
9:02
Nate The Lawyer
4 days ago $1.73 earnedHenyard Update - Police Chief Pleads Guilty & Rats To FBI On Super Mayor
21.9K8 -
 3:24:41
3:24:41
FreshandFit
14 hours agoShe Left A Great Situation. We Find Out Why! w/ Luke Belmar
288K38 -
 1:34:15
1:34:15
Badlands Media
17 hours agoBaseless Conspiracies Ep. 171: The Lady Bird Lake Murder Mystery
98.6K33