Premium Only Content
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
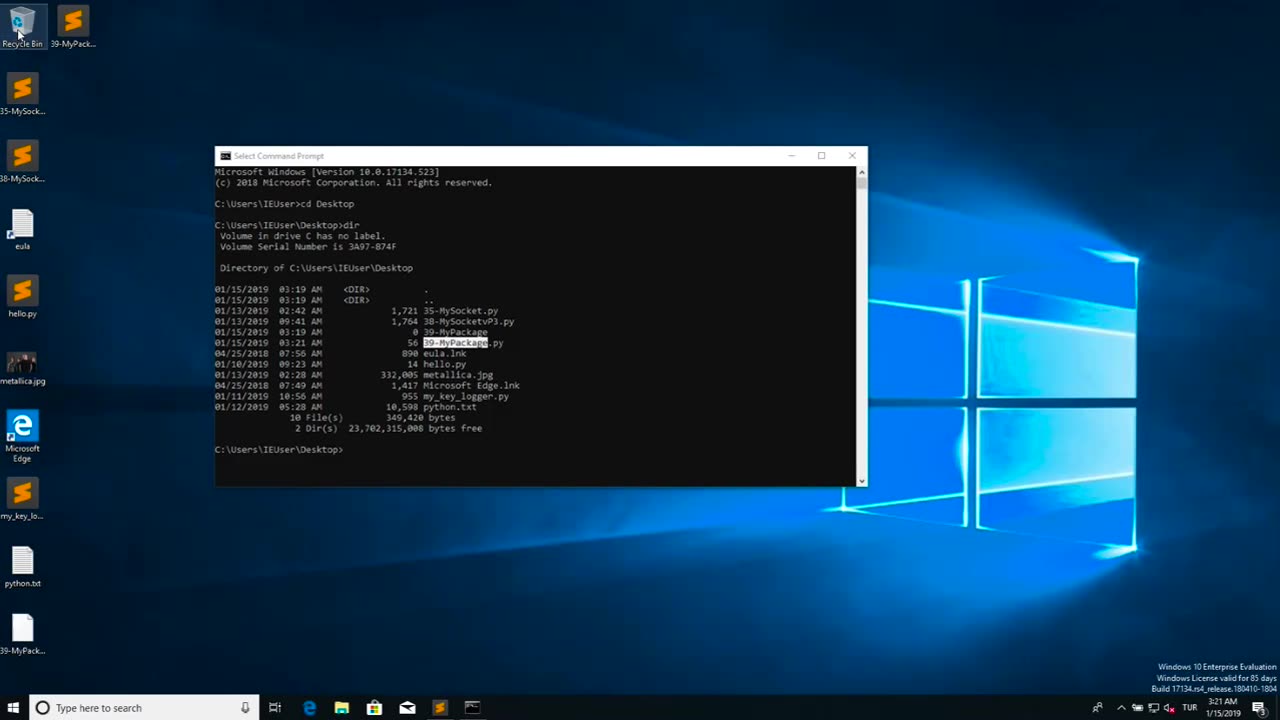
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Right Side Broadcasting Network
2 days agoLIVE: President Trump to Deliver Remarks in Rocky Mount, NC - 12/19/25
4,000 watching -
 LIVE
LIVE
VapinGamers
2 hours ago $0.03 earnedDestiny 2 - Dungeons and Loot with Friends - !rumbot !music
2,246 watching -
 2:07:44
2:07:44
TimcastIRL
2 hours agoTrump's Secret Plan To Make Charlie Kirk VP, America Fest IN CIVIL WAR | Timcast IRL
176K106 -
 LIVE
LIVE
I_Came_With_Fire_Podcast
11 hours agoLive Fire: Christmas Special
153 watching -
 46:26
46:26
Sarah Westall
5 hours agoWhat’s Behind the Silver Surge? Large Institutions Cashing In w/ Andy Schectman
4.03K -
 6:42:10
6:42:10
Turning Point USA
10 hours agoLIVE NOW: AMFEST DAY 2 - VIVEK, JACK POSOBIEC, MEGYN KELLY, ALEX CLARK AND MORE…
1.15M174 -
 LIVE
LIVE
Flyover Conservatives
21 hours agoHow to Win 2026 Before It Starts — Clay Clark’s Goal-Setting Blueprint | FOC Show
202 watching -
 12:52
12:52
The Kevin Trudeau Show Limitless
2 days agoBeyond Good And Bad: The Hidden Reality Code
40.2K18 -
 1:03:11
1:03:11
BonginoReport
6 hours agoBrown U Security Failures EXPOSED - Nightly Scroll w/ Hayley Caronia (Ep.201)
127K37 -
 51:09
51:09
Patriots With Grit
2 hours agoWill A.I. Replace Doctors? | Dr. Stella Immanuel MD
9.06K3