Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
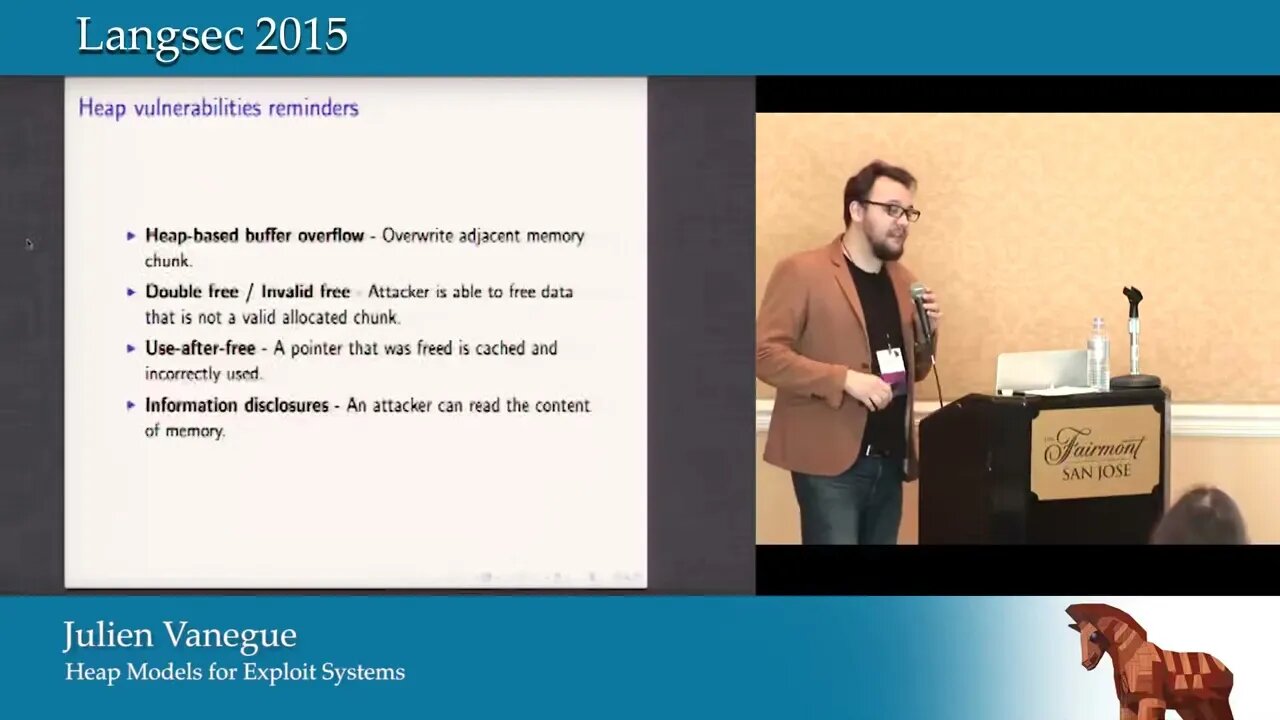
Heap Models for Exploit Systems
Loading comments...
-
 LIVE
LIVE
Badlands Media
8 hours agoDEFCON ZERQ Ep. 013
3,360 watching -
 LIVE
LIVE
Laura Loomer
2 hours agoEP149: Trump Frees the Hostages: Will HAMAS Respect the Ceasefire?
413 watching -
 LIVE
LIVE
SpartakusLIVE
4 hours agoLIVE from SUPER SECRET, VIP Location || BEACH FRONT into Verdansk
756 watching -
 LIVE
LIVE
Flyover Conservatives
21 hours ago"The Testosterone Levels of a Baby Bird" - America’s Health Crisis w/ Dr. Troy Spurrill | FOC Show
251 watching -
 LIVE
LIVE
PandaSub2000
1 day agoLIVE 10pm ET | SONIC RACING CROSSWORLDS with YOU!
94 watching -
 LIVE
LIVE
Drew Hernandez
6 hours agoDISGRACED SCOTUS REJECTS ALEX JONES' INFOWARS FREE SPEECH APPEAL
777 watching -

GrimmHollywood
4 hours ago🔴LIVE • GRIMM'S TUESDAY FRIGHT NIGHT with LEEMIDA • LITTLE NIGHTMARES 3 • PART 1 •
431 -

FusedAegisTV
2 hours agoGame & Rant #69 | CNN Mad Men Like To Look At Women, Nurse Joy Blackface? WTF Pokémon
325 -
 45:11
45:11
MattMorseTV
4 hours ago $19.37 earned🔴Dems. MELT DOWN over LEAKED MESSAGES.🔴
86.7K87 -
 LIVE
LIVE
SOLTEKGG
1 hour ago🔴LIVE - MORNING BATTLEFIELD 6 | Best BF6 settings
9 watching