Premium Only Content
SQL Injection Crash Course: Mastering SQLi for Enhanced Web Security
SQL Injection Crash Course: Mastering SQLi for Enhanced Web Security" is a comprehensive and practical guide designed to empower web developers, security professionals, and aspiring hackers with the knowledge and skills needed to defend against SQL Injection (SQLi) attacks.
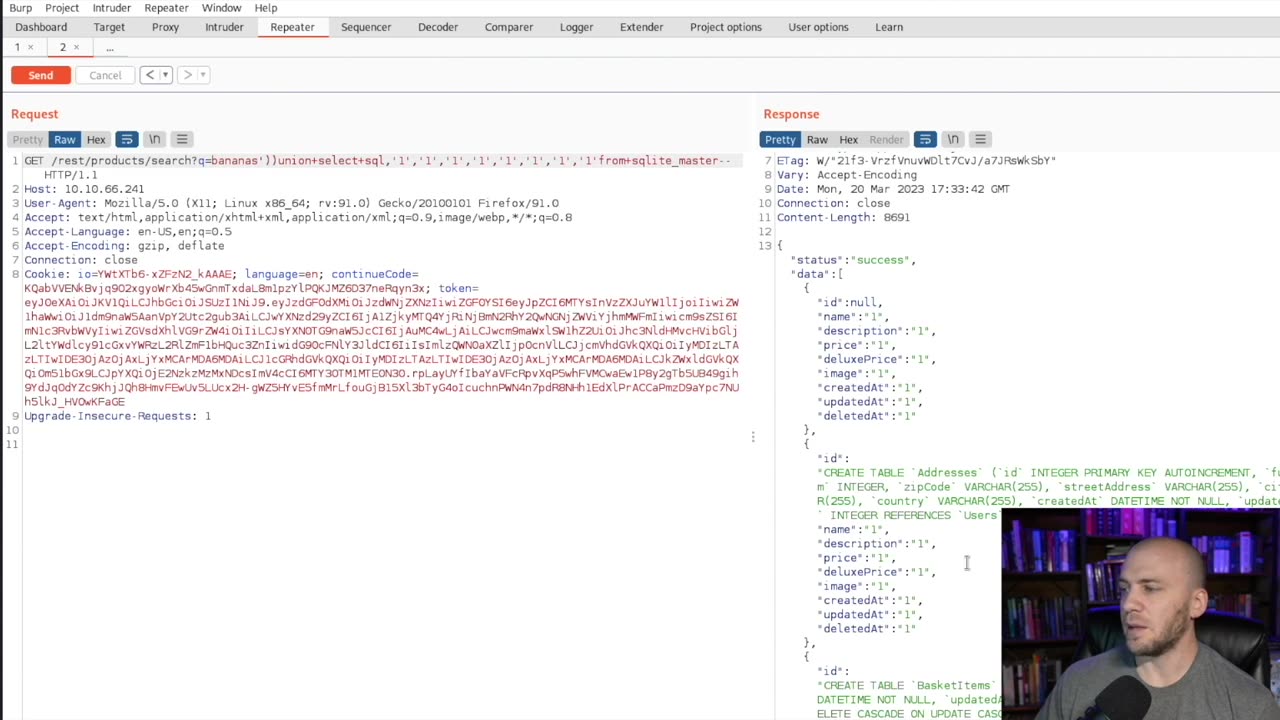
SQL Injection is a prevalent and highly exploitable vulnerability that targets the backend databases of web applications. This crash course delves deep into the inner workings of SQLi, equipping learners with a solid understanding of how these attacks occur and the potential consequences they can have on data integrity, confidentiality, and overall system security.
Through a combination of theoretical explanations, real-world examples, and hands-on exercises, participants will learn the art of identifying and exploiting SQL Injection vulnerabilities. From basic concepts like query manipulation to advanced techniques involving blind SQLi and time-based attacks, this crash course covers a wide range of attack vectors and strategies employed by both attackers and defenders.
Furthermore, the course goes beyond mere exploitation by emphasizing the significance of secure coding practices and robust defensive measures. Participants will gain insights into effective methods for preventing and mitigating SQL Injection vulnerabilities, such as input validation, parameterized queries, and proper access controls.
Whether you're a web developer aiming to fortify your applications against SQL Injection attacks, a security professional seeking to bolster your penetration testing skills, or an aspiring hacker looking to understand the intricacies of SQLi, this crash course provides the essential knowledge and tools to enhance web security and protect against one of the most prevalent and damaging attack vectors in the digital landscape.
Join us on this exhilarating journey into the realm of SQL Injection and emerge with the expertise needed to build resilient web applications, uncover vulnerabilities, and safeguard critical data from malicious exploits.
Tags: SQL Injection, SQLi, Web Security, Vulnerabilities, Exploitation, Data Integrity, Data Confidentiality, Secure Coding, Penetration Testing, Query Manipulation, Blind SQLi, Time-Based Attacks, Input Validation, Parameterized Queries, Access Controls.
-
 10:52
10:52
Code Blue Cam
1 day agoWhen You’re Too Drunk to Realize You Crashed into a Cop
8.38K9 -
 12:21
12:21
Isabella Moody
9 hours agoDave Smith and Nick Fuentes' BRUTAL Friendship Collapse Caught LIVE!
9.09K28 -
 50:52
50:52
Man in America
11 hours agoEpstein Files Reveal Human Cloning, MK-Ultra & Rothschilds Hiding HITLER??
245K110 -
 1:48:59
1:48:59
Badlands Media
15 hours agoDEFCON ZERQ Ep. 029: Epstein Files, WITSEC, and the Architecture of Control
105K67 -
 1:30:58
1:30:58
Inverted World Live
14 hours agoEpstein Worked for Rothschilds & Funded Child Trauma Psychic Ability Experiments | Ep. 166
107K31 -
 3:07:48
3:07:48
TimcastIRL
10 hours agoITS OUT OF CONTROL | Timcast IRL #1441
273K136 -
 3:09:43
3:09:43
Laura Loomer
9 hours agoEP169: Democrat Donors And Global Elites EXPOSED In Epstein Files
64.2K24 -
 53:39
53:39
Isabella Moody
8 hours agoNick Fuentes vs Sneako & Jake Shields: Epstein Drama Turns Allies into Enemies!
40.4K16 -
 2:12:20
2:12:20
TheSaltyCracker
10 hours ago$8K Wayfair Cabinets are Back ReeEStream 02-03-26
164K228 -
 2:29:28
2:29:28
Joker Effect
9 hours agoRUMBLESHORTS ARE COMING TOMORROW! Let's talk about it! Do NOT miss the boat!
49.7K2