Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
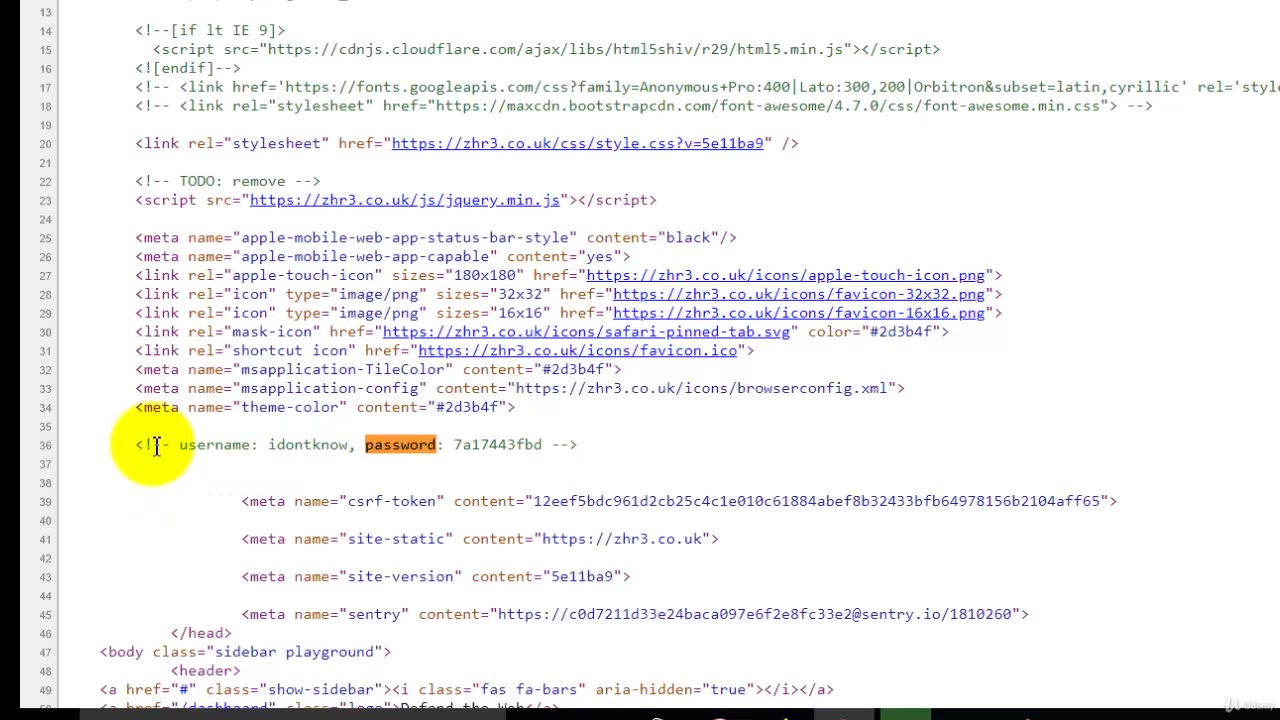
Learn Ethical Hacking - Chapter 2 - 1. Intro 1 (Client code information leak)
2 years ago
1
Ethical Hacking
Reverse Engineering
Cybersecurity
Penetration Testing
Security Auditing
Network Security
Information Security
Hacking Techniques
Vulnerability Assessment
Exploit Development
Malware Analysis
Download resource files here: https://mega.nz/file/WMdWiBAR#oiiOZ0JxvsWkKOGT7tgw0ezYmH8KFjGIkeKrAOsnKI4
Password for the file is : rumble.com/sastecourses
Loading comments...
-
 LIVE
LIVE
Steven Crowder
3 hours ago🔴 Charlie Kirk Conspiracies Spread Like Wildfire: What's Really Going On?
86,780 watching -
 LIVE
LIVE
Right Side Broadcasting Network
1 hour agoLIVE: White House Press Secretary Karoline Leavitt Holds a Press Briefing - 9/22/25
1,589 watching -
 LIVE
LIVE
Nerdrotic
4 hours agoStar Wars: Mandalorian and Grogu Trailer Reaction - Nerdrotic Nooner 518
221 watching -
 1:04:57
1:04:57
The Rubin Report
1 hour agoCrowd Stunned by Trump’s Brutally Honest Remark at Charlie Kirk’s Funeral
24.4K18 -
 LIVE
LIVE
Grant Stinchfield
58 minutes agoThe Exploitation of Charlie Kirk's Death is Very Real
144 watching -
 1:40:13
1:40:13
Nikko Ortiz
2 hours agoJapan's Prison System Is CRAZY...
7.84K4 -
 LIVE
LIVE
The Mel K Show
1 hour agoMORNINGS WITH MEL K Globalist Descend on America: Is it Time to Pull the Plug? 9-22-25
582 watching -
 LIVE
LIVE
The Shannon Joy Show
1 hour agoEpstein Cover Up - Kash Patel Has Names Of Epstein’s Pedophiles. Live Exclusive With Nick Bryant!
174 watching -
 LIVE
LIVE
LFA TV
15 hours agoLFA TV ALL DAY STREAM ! | MONDAY 9/22/25
4,649 watching -
 9:08
9:08
Hollywood Exposed
20 hours agoMatthew McConaughey Shocks ABC Host With Blunt Message to Democrats
442