Premium Only Content
Sublist3r Tutorial: Discover Subdomains with Ease
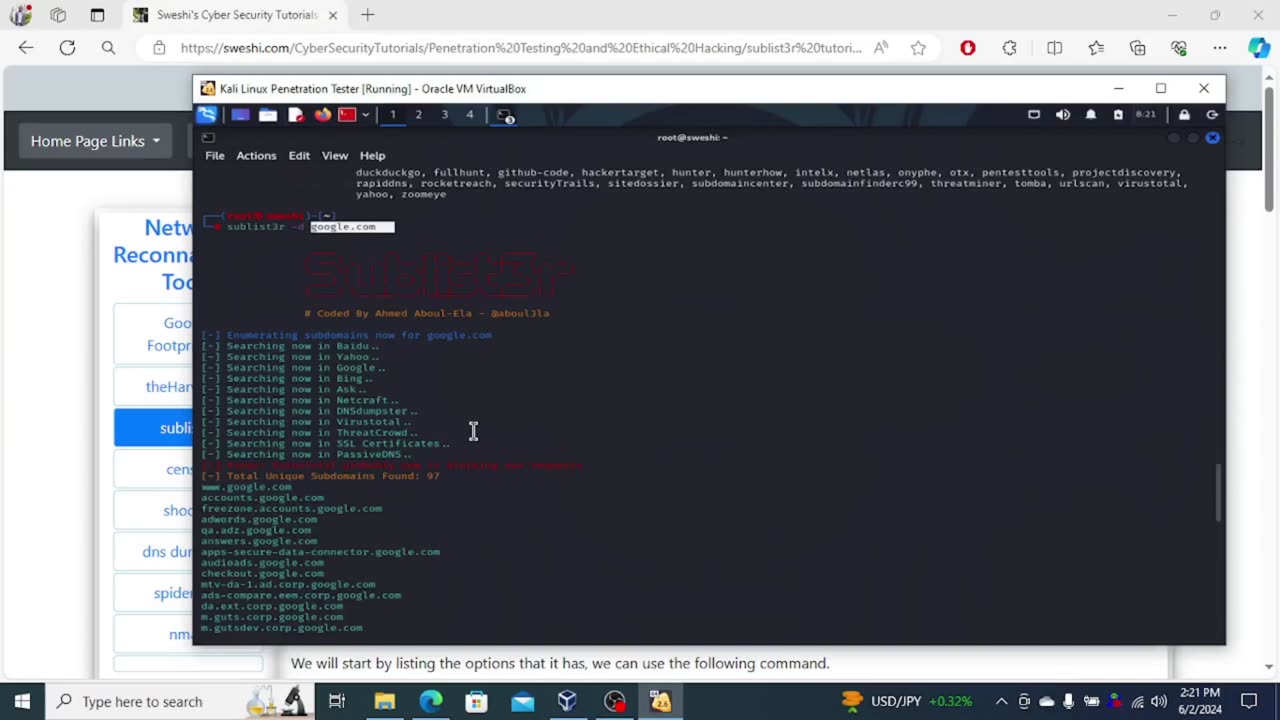
Sublist3r (commonly stylized as Sublist3r) is a tool included in Kali Linux for enumerating subdomains of websites, helping cybersecurity professionals in reconnaissance tasks.
SUBLISTER
00:17 - sublister introduction
01:00 - searching for subdomains of google
01:45 - results
02:12 - saving the results
02:38 - searching for domain names with open ports
03:25 - conclusion
Reconnaissance tutorials
Google Footprinting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/GoogleFootprinting.php
theHarvester tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/theHarv3ster%20-%20Network%20Reconnaissance%20tool%20tutorial.php
sublister tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sublist3r%20tutorial.php
censys free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/censys%20tutorial.php
shodan free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/shodan%20tutorial.php
dns dumpster tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dns%20dumpster%20tutorial.php
spiderfoot tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/spiderfoot%20tutorial.php
nmap tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Nikto web server scanning Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Dirbuster web directory scanner Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dirbuster%20tutorial.php
Nmap port scanner:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Legion port scanner and vulnerability scanning tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/legion%20tutorial.php
hping3 packet crafting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/hping3%20tutorial.php
amap scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/amap%20tutorial.php
masscan fast port scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/masscan%20tutorial.php
netcat tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/netcat%20tutorial.php
VULNERABILITY SCANNING TUTORIALS
Nessus tenable tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nessus%20tenable%20essentials%20tutorial.php
Nikto tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Exploit tools:
Metasploit beginner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/metasploit%20tutorial.php
SQL Map tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sqlmap%20tutorial.php
routersploit tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/routersploit.php
FORENSIC INVESTIGATION TOOLS:
Wireshark Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/wireshark%20tutorial.php
LastActivityView tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/lastActivityView%20tutorial.php
Process Monitor Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/Process%20Monitor%20Tutorial.php
Autoruns Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/autoruns%20tutorial.php
-
 57:01
57:01
Coin Stories with Natalie Brunell
17 hours agoSamourai CEO Keonne Rodriguez: Guilty Plea, Prison Ahead, and the Fight for Privacy in Bitcoin
8.69K -
 53:33
53:33
Dialogue works
2 days ago $0.98 earnedMatthew Hoh: Inside the New U.S. National Security Strategy: Realities, Risks, and Flaws
3.14K5 -
 2:19:51
2:19:51
Side Scrollers Podcast
18 hours agoSmashJT CRASHES The Game Awards 2025 + Full Show Recap with Vara Dark + More | Side Scrollers
60.2K9 -
 10:11
10:11
MattMorseTV
14 hours ago $8.07 earnedThe Documents just got UNSEALED…
12.7K34 -
 14:55
14:55
Nikko Ortiz
13 hours agoI Laugh I Go To Hell...
11.6K1 -
 23:45
23:45
GritsGG
20 hours agoMost OP Weapon In Warzone History? USE NOW!
7.56K -
 1:12:47
1:12:47
MetatronGaming
6 days agoNo, I'm not Human PART 2 ENDING
10.2K -
 3:55:52
3:55:52
PandaSub2000
2 days agoMetroid Prime 4: Beyond | ULTRA BEST AT GAMES (Original Live Version)
7.96K3 -
 13:16
13:16
The Pascal Show
10 hours ago $2.22 earned'CANDACE, STOP LYING!' Erika Kirk Demands Candace Owens Stop Spreading Lies about Charlie Kirk
10.1K13 -
 LIVE
LIVE
Lofi Girl
2 years agoSynthwave Radio 🌌 - beats to chill/game to
706 watching