Premium Only Content
Sublist3r Tutorial: Discover Subdomains with Ease
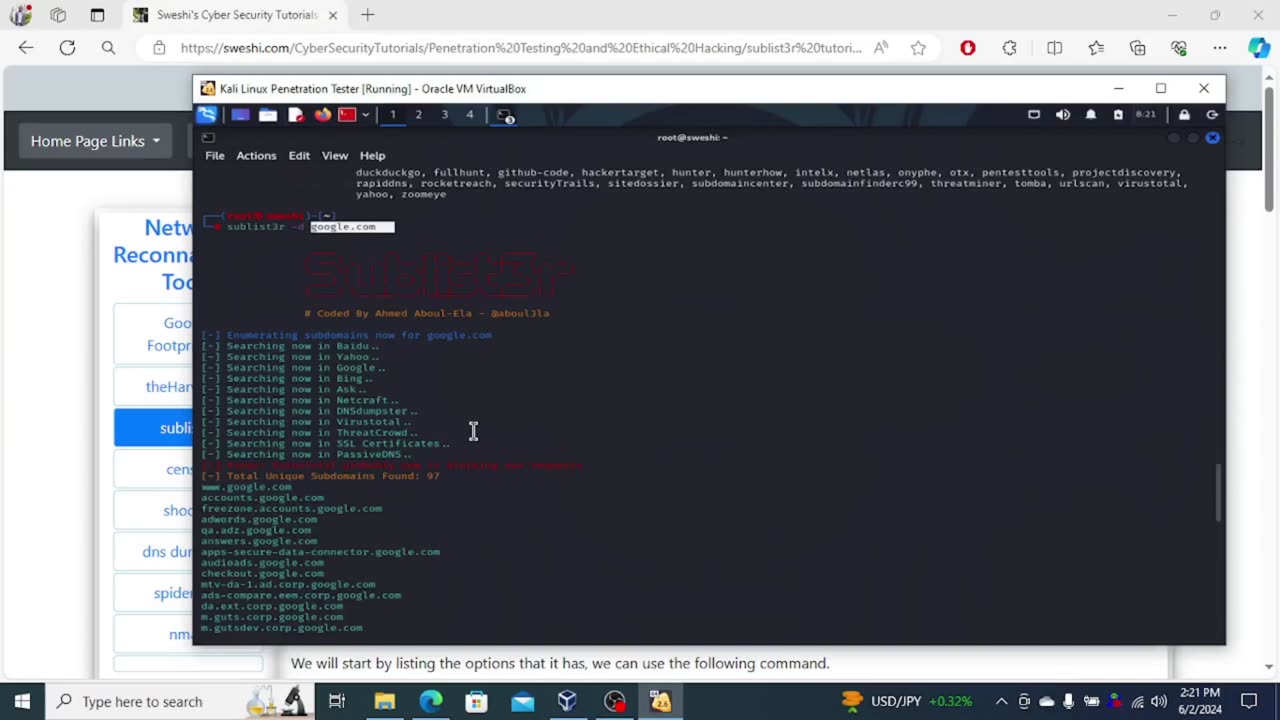
Sublist3r (commonly stylized as Sublist3r) is a tool included in Kali Linux for enumerating subdomains of websites, helping cybersecurity professionals in reconnaissance tasks.
SUBLISTER
00:17 - sublister introduction
01:00 - searching for subdomains of google
01:45 - results
02:12 - saving the results
02:38 - searching for domain names with open ports
03:25 - conclusion
Reconnaissance tutorials
Google Footprinting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/GoogleFootprinting.php
theHarvester tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/theHarv3ster%20-%20Network%20Reconnaissance%20tool%20tutorial.php
sublister tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sublist3r%20tutorial.php
censys free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/censys%20tutorial.php
shodan free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/shodan%20tutorial.php
dns dumpster tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dns%20dumpster%20tutorial.php
spiderfoot tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/spiderfoot%20tutorial.php
nmap tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Nikto web server scanning Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Dirbuster web directory scanner Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dirbuster%20tutorial.php
Nmap port scanner:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Legion port scanner and vulnerability scanning tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/legion%20tutorial.php
hping3 packet crafting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/hping3%20tutorial.php
amap scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/amap%20tutorial.php
masscan fast port scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/masscan%20tutorial.php
netcat tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/netcat%20tutorial.php
VULNERABILITY SCANNING TUTORIALS
Nessus tenable tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nessus%20tenable%20essentials%20tutorial.php
Nikto tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Exploit tools:
Metasploit beginner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/metasploit%20tutorial.php
SQL Map tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sqlmap%20tutorial.php
routersploit tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/routersploit.php
FORENSIC INVESTIGATION TOOLS:
Wireshark Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/wireshark%20tutorial.php
LastActivityView tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/lastActivityView%20tutorial.php
Process Monitor Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/Process%20Monitor%20Tutorial.php
Autoruns Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/autoruns%20tutorial.php
-
 DVR
DVR
The Rubin Report
1 hour agoListen to the Fear in Whoopi Goldberg’s Voice on 'The View' as She Gives a Chilling Warning
11.2K25 -
 LIVE
LIVE
The Mel K Show
1 hour agoMORNINGS WITH MEL K - Constitution Incompatible with Globalist Goals 9-16-25
537 watching -
 LIVE
LIVE
Grant Stinchfield
1 hour agoRFK Jr. Speaks Out: The Pain of Assassination & the Loss of Charlie Kirk
95 watching -
 1:59:33
1:59:33
Benny Johnson
2 hours agoKash Patel Testifying LIVE Now on Charlie Kirk Assassination, Trump to Declare Antifa TERRORISTS?!
32K39 -
 2:07:38
2:07:38
Timcast
3 hours ago🚨LIVE: Kash Patel Testifies Over Charlie Kirk Assassination In Senate | Tim Pool
56.7K54 -
 LIVE
LIVE
Trumpet Daily
43 minutes agoTrumpet Daily LIVE | Sept. 16, 2025
471 watching -
 LIVE
LIVE
The Shannon Joy Show
1 hour agoTrojan Horse Trump Pushing ‘Worse Than Biden’ Speech Control Using Kirk Killing. Guest Brett Miller
223 watching -
 1:01:35
1:01:35
VINCE
3 hours agoThe Left's 'Malignant' Violence Problem | Episode 126 - 09/16/25
191K102 -
 LIVE
LIVE
LFA TV
6 hours agoLFA TV ALL DAY STREAM - TUESDAY 9/16/25
4,453 watching -
 1:45:59
1:45:59
Dear America
4 hours agoKiller ADMITS To Killing Charlie In DISCORD. Terror Cell EXPOSED! + JD Fills In on Charlie’s Show!
148K83