Premium Only Content
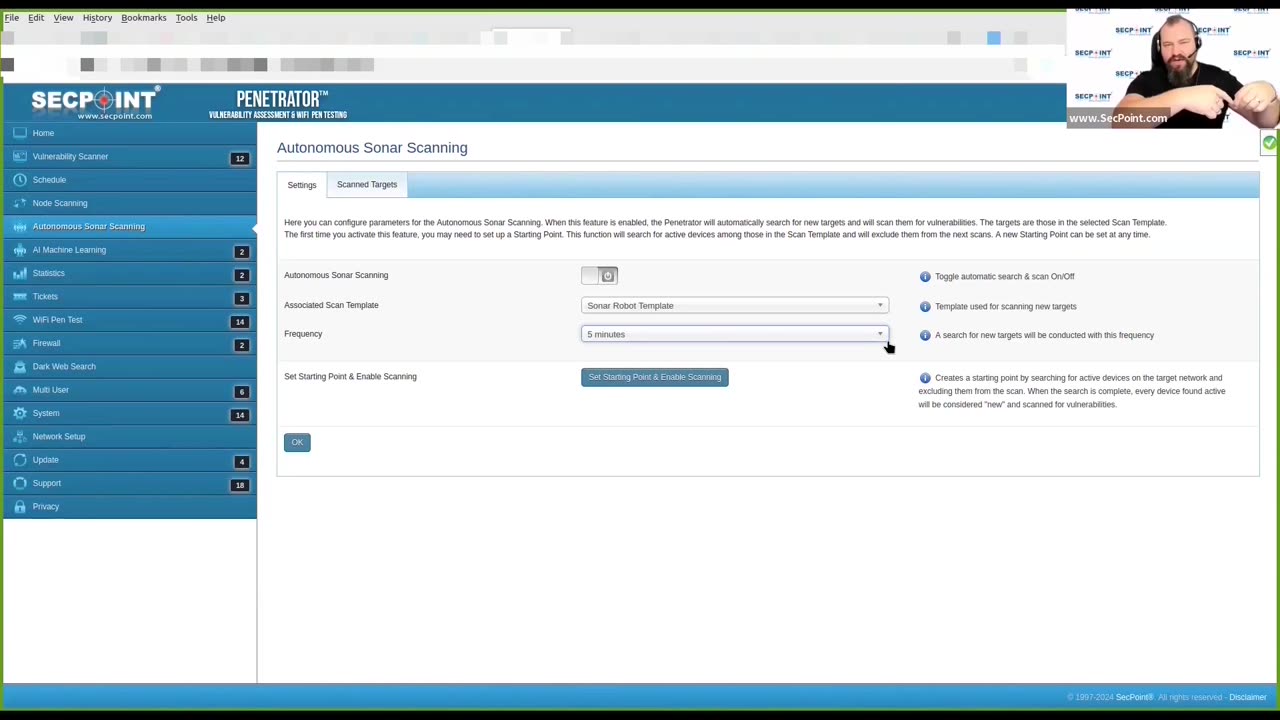
🛡️ SecPoint® Penetrator – Sonar Detect Hostile Devices
In this video, we show how the powerful Sonar feature in the SecPoint Penetrator can help detect unauthorized or hostile devices connected to your network.
Quickly identify suspicious activity such as:
✅ A new Linux device appearing on a Windows-only environment
✅ Unknown systems joining your network segment
✅ Devices plugged in without permission – potential insider threats
The Sonar scan is ideal for securing sensitive environments by actively monitoring connected devices and flagging anomalies before damage is done.
💻 Key Features of the SecPoint Penetrator:
✅ Authenticated Vulnerability Scanning via SSH
✅ Supports Cisco, Linux, NetBSD, OpenBSD & FreeBSD
✅ Detects Missing Patches, Weak Configurations & More
✅ Customizable Reports – Export in .txt, .html, .pdf formats
✅ Fully On-Premise – No cloud, no data leaks
✅ Easy compliance with 33+ scanning profiles
✅ Includes Dark Web Search & WiFi Testing
🔗 Explore More:
https://www.secpoint.com/penetrator.html
🎁 Try Our Free Online Vulnerability Scan:
https://www.secpoint.com/free-vulnerability-scan.php
https://www.secpoint.com/contact-me.php
📣 Stay Connected:
🔹 Twitter (X): https://x.com/secpoint
🔹 LinkedIn: https://www.linkedin.com/company/secpoint
👍 Like, Share & Subscribe for the latest in cybersecurity and vulnerability scanning!
#CyberSecurity #SecPoint #Penetrator #SonarScan #HostileDeviceDetection #NetworkMonitoring #InsiderThreat #VulnerabilityScanner #ITSecurity #CyberDefense
-
 35:33
35:33
Stephen Gardner
4 hours agoThe Supreme Court Just Changed History FOREVER!
35.9K57 -
 1:16:31
1:16:31
Kim Iversen
3 hours agoTucker: Egyptian Planes Trailed Erika Kirk for Years
26.3K53 -
 LIVE
LIVE
Mally_Mouse
1 day ago🎮 Let's Play!!: Stardew Valley pt. 36
110 watching -
 LIVE
LIVE
Quite Frankly
6 hours agoENDING Income Tax, Rejected Amendments, Reels & OPEN LINES | KrisAnne Hall 12/10/25
520 watching -
 55:09
55:09
American Thought Leaders
2 hours agoA Neurosurgeon’s Proof of an Immortal Soul | Dr. Michael Egnor
5.88K3 -
 LIVE
LIVE
The Mike Schwartz Show
3 hours agoTHE MIKE SCHWARTZ SHOW Evening Edition 12-10-2025
697 watching -
 LIVE
LIVE
SavageJayGatsby
2 hours agoModded Minecraft Chaos with the Wife 🌋💎
141 watching -
 6:42:34
6:42:34
Dr Disrespect
8 hours ago🔴LIVE - DR DISRESPECT - TARKOV 1.0 - DEAL OR NO DEAL
93.9K14 -
 1:03:56
1:03:56
The Amber May Show
6 hours agoTruth Under Fire: Exposing the War on Kids, Cancer, and Medical Freedom
9.3K3 -
 1:16:32
1:16:32
Russell Brand
5 hours agoThe Data They Don’t Want to Talk About | Dr John Campbell - SF661
151K78