Premium Only Content
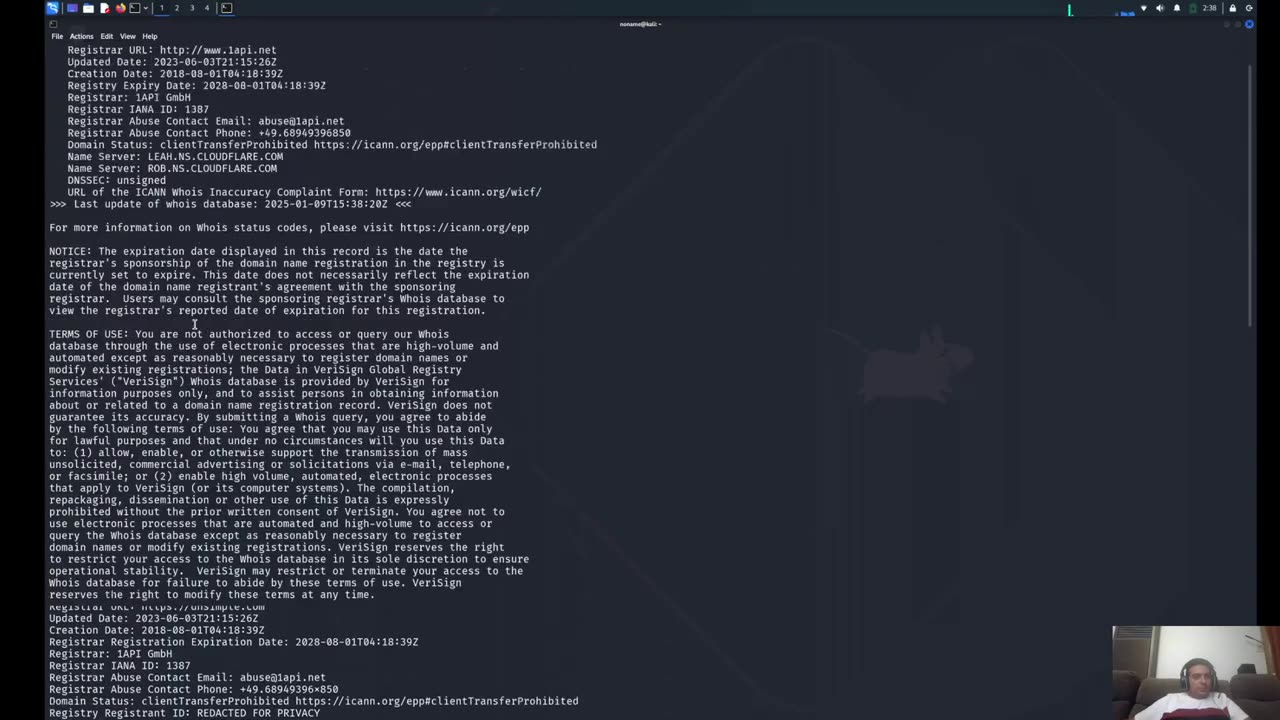
9.Whois - 10 1 2025
🌐 Master Domain Reconnaissance with Whois | Kali Linux Tutorial 🔥
Welcome to our in-depth guide on the Whois tool in Kali Linux—an essential command-line utility used for gathering information about domain names, IP addresses, and network ownership. Perfect for ethical hackers, penetration testers, and cybersecurity analysts! 🚀
🎯 What You'll Learn:
✅ What is Whois and how it works
✅ How to install and use Whois in Kali Linux
✅ Performing basic and advanced Whois lookups
✅ How to gather critical information about domain owners, registrars, and expiration dates
✅ Using Whois for reconnaissance in penetration testing
✅ Real-world examples for ethical hacking and intelligence gathering
✅ Best practices and ethical considerations for responsible usage
🔐 Why Use Whois?
Domain Ownership Details: Retrieve information like registrant names, contact details, and domain expiration.
Network Information: Gather insights about IP ranges, autonomous system numbers (ASN), and hosting providers.
First Step in Reconnaissance: Essential for footprinting during penetration testing.
Quick and Lightweight: Instantly fetch critical information with just a simple command.
Don't forget to subscribe to our YouTube channel for video tutorials, live sessions, and more interactive content.
Welcome to CyberSec Insights: Your Guide to Cybersecurity and Hacking Tricks!
Explore the fascinating world of cybersecurity with our comprehensive blog. Designed for everyone from beginners to seasoned professionals, we provide the latest security trends, hacking techniques, and practical tips to protect yourself and your organization. Our in-depth tutorials, expert advice, and real-world applications will enhance your skills and keep you ahead in the ever-evolving cyber landscape.
Join us on a journey to uncover the secrets of cybersecurity, empowering you with the tools and knowledge to secure the digital realm. Stay informed, stay safe!
#ciscorouter #cisco #router #routersetup #cybersecurity #cyberprotection #cybersecurityawareness #technology #technicalsupport #msp #microsoft #apple #informationsecurity #informationtechnology #stmonicait
-
 1:03:30
1:03:30
BonginoReport
1 hour agoCould This Be The End Of The Protests? | Episode 217 - 02/03/26 VINCE
38.4K28 -
 DVR
DVR
Chad Prather
16 hours agoThe Weight of Authority: Who’s Really in Charge?
11.5K13 -
 LIVE
LIVE
The Chris Salcedo Show
15 hours agoGOP Surrenders On Election Integrity: Is The Uniparty Fix In?
925 watching -
 13:08
13:08
Nate The Lawyer
20 hours ago $0.14 earnedThe Government's Case Against Don Lemon's Violation Of The Klan Act
1.29K7 -
 LIVE
LIVE
LFA TV
11 hours agoLIVE & BREAKING NEWS! | TUESDAY 2/3/26
2,435 watching -
 2:01:20
2:01:20
Steven Crowder
1 day agoWhite Replacement is Real: But It's Much Bigger than You Think
875K525 -
 40:10
40:10
ZeeeMedia
15 hours agoWHO Just Planned the Next Pandemic: How Epstein is Connected | Daily Pulse Ep 188
16K25 -
 39:02
39:02
Connor Tomlinson
22 hours agoThe Right Has a Young White Male Problem
12.4K8 -
 14:29
14:29
VSOGunChannel
13 hours ago $0.56 earnedShould You Be Bulking Out Ammo Right Now?
11.5K7 -
 0:29
0:29
WildCreatures
1 day ago $0.49 earnedPregnant jaguar with injured jaw hunts along riverbank
13.4K8