Premium Only Content
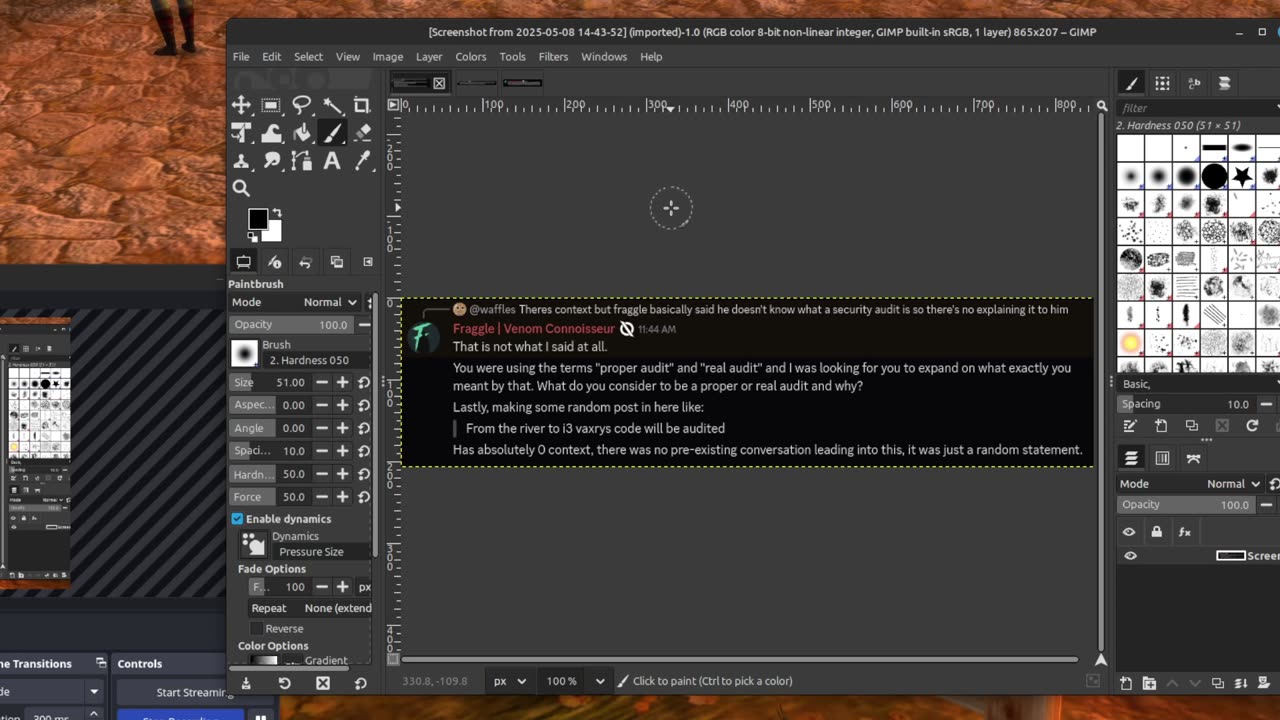
from the river to i3, hyprland will get an audit
reading:
https://github.com/hyprwm/Hyprland/blob/main/src/plugins/HookSystem.cpp#L140-L223 Suspicious homebrew malloc system instead of properly handling plugins
https://github.com/hyprwm/Hyprland/blob/main/src/plugins/HookSystem.cpp#L225-L229 non-portable plugin system
https://github.com/hyprwm/Hyprland/blob/main/src/plugins/PluginAPI.cpp#L315-L321 shelling out to fucking nm to read symbols (incredibly cursed)
execAndGet is a bad programming practice to just use left right and center as can been seen by vulnerability https://nvd.nist.gov/vuln/detail/CVE-2024-42029 which was caused by exposing untrusted inputs (i.e. window titles) to execAndGet without sanitizing properly, showing why this kinda shit can be a concerning practice
But also more importantly
https://bugs.gentoo.org/930831#c6
Poor response and acknowledgement of security issues (granted he responded to the portal one well)
tl;dr Hyprland has trying to mark its stack memory executable for some reason
malloc does not check for nullptr but moriginal_bytes cannot be null
-
 LIVE
LIVE
Mally_Mouse
3 hours ago🌶️ 🥵Spicy BITE Saturday!! 🥵🌶️- Let's Play: Minecraft Christmas Adventure!!
3,086 watching -
 2:14:31
2:14:31
Side Scrollers Podcast
8 hours agoSide Scrollers INVITE ONLY - Live From Dreamhack
149K9 -
 1:18:23
1:18:23
Simply Bitcoin
2 days ago $13.38 earnedThe Bitcoin Crucible w/ Alex Stanczyk and Lawrence Lepard
32.4K4 -
 1:25:03
1:25:03
Jeff Ahern
8 hours ago $20.11 earnedThe Saturday Show with Jeff Ahern
93.7K13 -
 1:31:56
1:31:56
Michael Franzese
23 hours agoWill NBA do anything about their Gambling Problems?
146K28 -
 57:26
57:26
X22 Report
12 hours agoMr & Mrs X - The Food Industry Is Trying To Pull A Fast One On RFK Jr (MAHA), This Will Fail - EP 14
126K77 -
 2:01:08
2:01:08
LFA TV
1 day agoTHE RUMBLE RUNDOWN LIVE @9AM EST
174K15 -
 1:28:14
1:28:14
On Call with Dr. Mary Talley Bowden
10 hours agoI came for my wife.
45.7K37 -
 1:06:36
1:06:36
Wendy Bell Radio
15 hours agoPet Talk With The Pet Doc
85K37 -
 30:58
30:58
SouthernbelleReacts
3 days ago $9.64 earnedWe Didn’t Expect That Ending… ‘Welcome to Derry’ S1 E1 Reaction
57.8K12