Premium Only Content
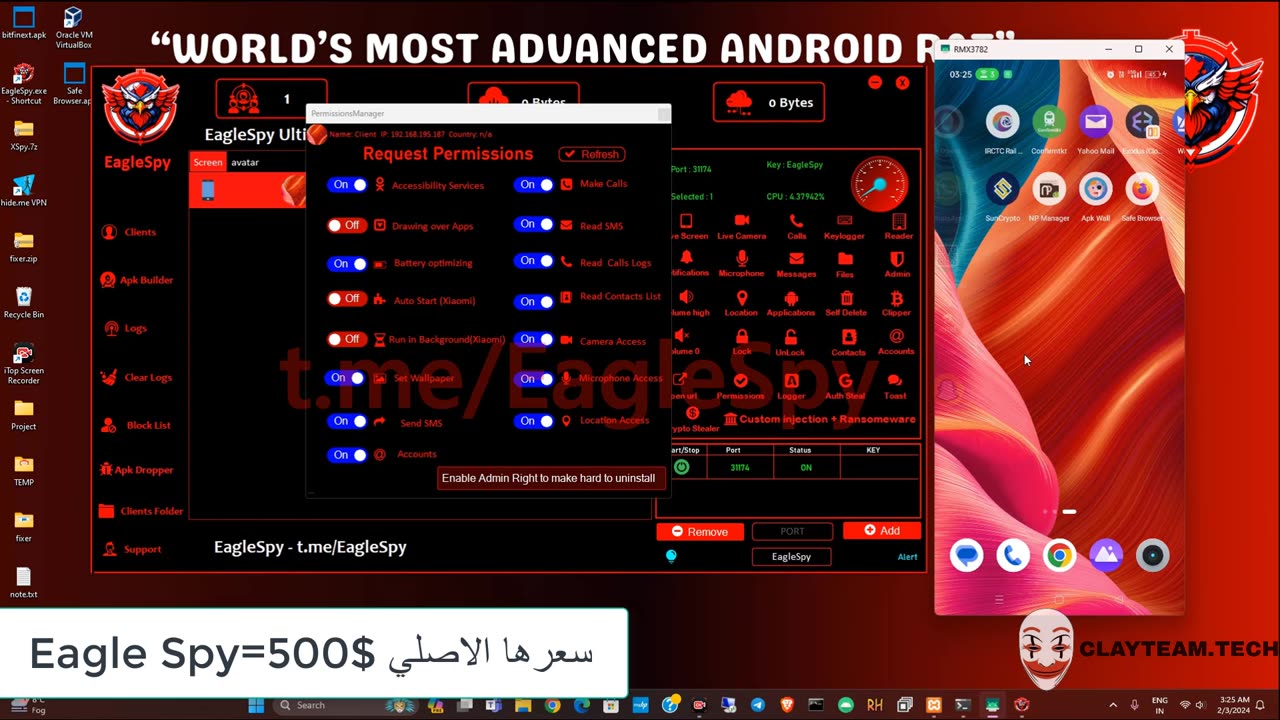
CraxsRat v7.4 VIP & Spyroid VIP & EagleSpy & G-700
WhatsApp: [https://api.whatsapp.com/send?phone=201063805787]
Join the “cool people” group and follow all the latest in penetration testing:
[https://chat.whatsapp.com/JWZsLE0U07l81Kd0HgNyU4]
**Unleash the Power of Ethical Cybersecurity Tools**
🔒 **Elevate Your Security Game** with an exclusive deep‑dive into five cutting‑edge platforms: **CraxsRat v7.6**, **Spyroid VIP**, **EagleSpy**, **G‑700**, and **Full Source Code**.
> **Disclaimer**: These solutions are **extremely potent** and designed **only for lawful, professional use**. Misuse is illegal and unethical. Always secure **explicit authorization** before conducting any tests or deployments.
---
## 🚀 Why This Collection Matters
* **Total Visibility**: From remote device control to network forensics, gain insight into real‑world attack vectors.
* **Hands‑On Learning**: Analyze source code to reverse‑engineer techniques and strengthen your defensive posture.
* **Compliance & Ethics**: Master best practices to stay fully compliant with GDPR, CCPA, CFAA, and international standards.
---
## 🔍 Deep‑Dive: Feature Highlights
### 1. CraxsRat v7.6
* 🔧 **Remote Access Trojan** with encrypted C2 channels
* 🎥 Live screen capture, keylogging, camera/mic hijacking
* 🔄 Persistent backdoor for full system oversight
> **Use Case**: Security teams can pinpoint vulnerabilities, refine incident response, and build AI‑powered threat detection.
### 2. Spyroid VIP
* 📡 Real‑time GPS tracking & geofencing
* 💬 Social media & call monitoring (WhatsApp, Telegram, etc.)
* 👻 Stealth mode: zero icon footprint
> **Use Case**: Enterprise device management and parental controls (with clear consent).
### 3. EagleSpy & G‑700
* 🌐 Wi‑Fi cracking, MITM simulations
* 🎣 Phishing‑style credential harvesting
* 🔓 Exploit unpatched CVEs
> **Use Case**: Ethical hackers perform red‑team assessments, patch security gaps, and educate stakeholders.
### 4. Full Source Code
* 🛠️ Build custom defenses (antivirus signatures, IDS rules)
* 🔍 Dissect malicious logic to turbo‑charge threat intelligence
* 📚 Perfect for academic research and training
---
## 🛡️ Your Ethical Playbook
1. **Obtain Written Consent** before any engagement.
2. **Focus on Defense**: Harden networks, deploy IDS/IPS, and run tabletop exercises.
3. **Secure & Audit** your code repositories—limit access to vetted professionals.
4. **Report Responsibly**: Disclose zero‑days to CERTs or participate in bug bounties.
---
## 🌎 Join the Global Cybersecurity Movement
* **Organizations**: Adopt Zero‑Trust, enforce MFA, and schedule regular red‑team drills.
* **Professionals**: Keep software patched, practice end‑to‑end encryption, and stay vigilant.
* **Developers**: Contribute to open‑source security projects like OWASP and champion ethical coding.
**Ready to transform your cybersecurity strategy?** Dive in, stay ethical, and fortify your digital fortress!
#Cybersecurity
#EthicalHacking
#InfoSec
#PenetrationTesting
#RAT
#RemoteAccess
#CraxsRat
#SpyroidVIP
#EagleSpy
#G700
#MalwareAnalysis
#ThreatIntelligence
#RedTeam
#BlueTeam
#SecurityResearch
#SourceCode
#CodeAudit
#NetworkSecurity
#WiFiHacking
#MITMAttack
#PhishingSimulation
#GDPR
#CCPA
#CFAA
#ZeroTrust
#MFA
#IDS
#IPS
#EndpointSecurity
#MobileSecurity
#AndroidSecurity
#iOSSecurity
#Geofencing
#Keylogging
#Backdoor
#EncryptedC2
#StealthTech
#PrivacyProtection
#DigitalForensics
#VulnerabilityAssessment
#ExploitDevelopment
#SecurityAwareness
#CyberDefense
#BugBounty
#CERT
#OpenSourceSecurity
#OWASP
#SecurityTraining
#MalwareReverseEngineering
#EthicalUse
#LegalCompliance
-
 18:09
18:09
Forrest Galante
5 days agoI Survived 24 Hours In The World's Deadliest Jungle
191K30 -
 LIVE
LIVE
Lofi Girl
2 years agoSynthwave Radio 🌌 - beats to chill/game to
426 watching -
 2:15:09
2:15:09
Badlands Media
19 hours agoOnlyLands Ep. 27: Power Hour Hangover, Trump’s Wartime Shift, and Portland in Flames
118K26 -
 22:21
22:21
DeVory Darkins
8 hours ago $16.90 earnedRioters attack Portland ICE Facility as Democrats make shocking admission
26.7K118 -
 2:06:06
2:06:06
TimcastIRL
11 hours agoTrump DOJ Announces INTERVENTION In Portland Over Nick Sortor Arrest | Timcast IRL
243K401 -
 6:53:58
6:53:58
SpartakusLIVE
13 hours ago#1 All-American HERO with LUSCIOUS hair and AVERAGE forehead brings Friday Night HYPE
70.4K7 -
 3:06:43
3:06:43
Laura Loomer
10 hours agoEP147: Islamic Terror EXPLODES In The West After UK Synagogue Attack
54.3K45 -
 1:02:50
1:02:50
Flyover Conservatives
16 hours agoEric Trump: America’s Most Subpoenaed Man SPEAKS OUT! | FOC Show
47K14 -
 3:36:44
3:36:44
PandaSub2000
1 day agoSuper Mario Galaxy 1 & 2 | ULTRA BEST AT GAMES (Original Live Version)
35.7K3 -
 1:26:04
1:26:04
Glenn Greenwald
14 hours agoJournalist Ken Klippenstein on Trump's New Domestic Terrorism Memo; Glenn Takes Your Questions on Bari Weiss's CBS Role, His Interview with Nick Fuentes, and More | SYSTEM UPDATE #526
102K86
