Premium Only Content
Making Putin's Cyber Attack Impossible (clarifying previous 2 vids) 2026-01-24 17-23-33
Realistically, the complexity and local differences in grids make a true, simultaneous “global” blackout extremely hard, but the same software, hardware targets, and methods above could credibly produce very large multi‑country blackouts if executed by capable state‑sponsored actors.
In summary, computers regulating power supply can effectively operate in "droop speed control" mode while disconnected from the internet by relying on local control systems. This approach enhances security and maintains essential power supply functions, though it may limit coordination and monitoring capabilities.
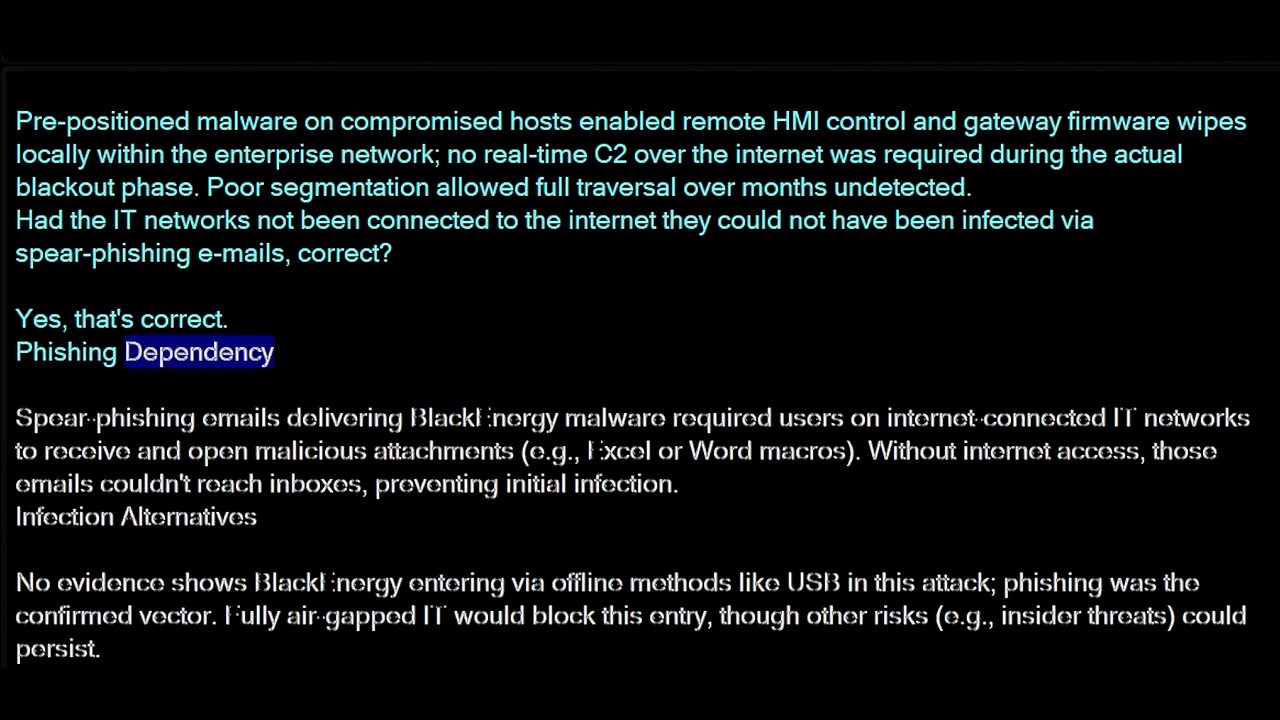
Pre-positioned malware on compromised hosts enabled remote HMI control and gateway firmware wipes locally within the enterprise network; no real-time C2 over the internet was required during the actual blackout phase. Poor segmentation allowed full traversal over months undetected.
Had the IT networks not been connected to the internet they could not have been infected via spear-phishing e-mails, correct?
Yes, that's correct.
Phishing Dependency
Spear-phishing emails delivering BlackEnergy malware required users on internet-connected IT networks to receive and open malicious attachments (e.g., Excel or Word macros). Without internet access, those emails couldn't reach inboxes, preventing initial infection.
Infection Alternatives
No evidence shows BlackEnergy entering via offline methods like USB in this attack; phishing was the confirmed vector. Fully air-gapped IT would block this entry, though other risks (e.g., insider threats) could persist.
-
 2:36:49
2:36:49
Barry Cunningham
6 hours agoSUNDAY NEWS ROUNDUP: President Trump Attends Wedding | Talk Shows Worried About Tulsi | And More!
58.9K36 -
 2:26:19
2:26:19
Nerdrotic
8 hours ago $6.39 earnedThe REDACTED Files Dropped | Dark Underworld Uncovered | Forbidden Frontier #127
52.6K10 -
 1:08:27
1:08:27
Sarah Westall
7 hours agoThe People Driving Canada’s MAID Program — And Why | Kelsi Sheren
20.5K5 -
 37:16
37:16
The HotSeat With Todd Spears
6 hours agoCrowned and Called with Kendra Spears
30.7K47 -
 2:37:07
2:37:07
IsaiahLCarter
11 hours ago $1.52 earnedCanceling Woke, in 2026 || APOSTATE RADIO 042 (Paul D. Rossi, Matthew Mastronardi)
23.1K1 -
 1:32
1:32
The Dan Bongino Show
11 hours agoDo I have scores to settle on my show? You're damn right
254K342 -
 14:34
14:34
Crowder Bits
1 day agoThis Is Why Democrats Can’t Win Without Open Borders
60.7K42 -
 1:30:59
1:30:59
The Attorney Andrew Branca Show
12 hours agoFederal Court: ICE WINS! MN LOSES! PLUS Federal ID Order!
73.9K41 -
 1:23:05
1:23:05
MattMorseTV
12 hours ago $50.07 earned🔴The Dems. have a "NEW STRATEGY."🔴
162K442 -
 13:20
13:20
Full Ahead
23 days ago $4.72 earnedMiami: The City of Tomorrow 4K Walking Tour
50.1K11