Premium Only Content
10X Your Cyber Defense - Understand the differences Common Hash Functions
Ignite unbreakable password security with powerful cryptographic hashing, salts, and digital signatures that protect logins, verify identity, prevent tampering, and boost cybersecurity for your accounts, apps, and cloud data online.
CHAPTERS
00:00 How Hashing Protects Passwords, Identities, and Secrets
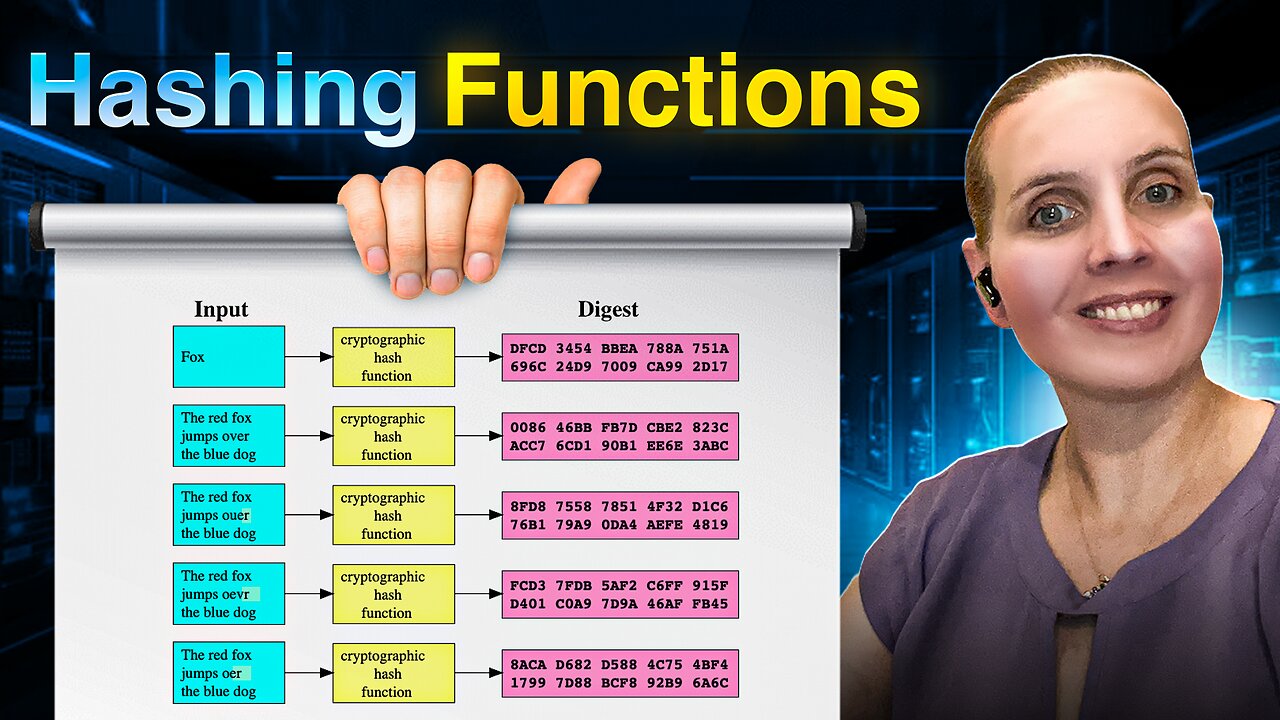
00:45 Hash Functions and Fingerprints: Turning Messages into Numbers
01:10 One‑Way Hashes: Why Hashes Cannot Be Reversed
01:25 Digital Signatures: Verifying Sender Identity and Authenticity
01:39 Non‑Repudiation: Proving Who Really Sent the Message
02:11 Password Hashing: How Websites Safely Store Passwords
02:33 What Is a Cryptographic Hash? Fixed‑Length Output Explained
02:45 Hash Properties, Salts, and Rainbow Table Protection
03:30 Hash Collisions: When Different Inputs Share the Same Fingerprint
03:48 Why MD5 Is Weak: Collisions, Cracking, and Legacy Use Only
05:07 SHA1, SHA256, SHA512: Modern Hash Algorithms Overview
05:49 Verifying File Integrity with SHA256 Checksums (Kali Example)
06:48 How Blockchains Use SHA256 to Link and Secure Blocks
06:59 SHA3 Sponge Construction: Absorbing and Squeezing Data
07:42 Bcrypt Overview: Adjustable Cost and Stronger Password Hashing
-
 LIVE
LIVE
TheCrucible
1 hour agoThe Extravaganza! EP: 91 with guest co-host Rob Noerr
1,976 watching -
 1:22:37
1:22:37
Redacted News
2 hours agoIs Epstein Still Alive? Bodies switched out! Melinda Gates Speaks Out Over Bill Gates | Redacted
114K57 -
 1:25:16
1:25:16
vivafrei
4 hours agoGeorge Zinn Pleads Guilty? Lawyers Explain Trucker Class Action Scandal! Epstein Fallout & MORE
103K14 -
 1:24:54
1:24:54
Michael Franzese
2 hours agoThe Boss Of Hells Angels: Sitdown With George Christie Part 2
20K -
 1:35:56
1:35:56
The Quartering
4 hours agoICE Starts Trolling Karens, Veggietales Woke Meltdown, The Death Of Junkfood & Creepy Epstein
150K29 -
 LIVE
LIVE
LFA TV
20 hours agoLIVE & BREAKING NEWS! | TUESDAY 2/3/26
1,422 watching -
 16:30
16:30
Stephen Gardner
5 hours agoDemocrats get NIGHTMARE NEWS as Trump EXPOSES Their Secrets!
35.6K33 -
 LIVE
LIVE
Drew Hernandez
15 hours agoTYLER ROBINSON HEARING: DEFENSE MOVES TO DISQUALIFY PROSECUTION
559 watching -
![[Ep 838] SAVE Act SAVES America – Nuke Filibuster! | Dems Rage Baiting BS | Zohran Policies Kill 16](https://1a-1791.com/video/fwe2/e4/s8/1/Q/P/q/W/QPqWz.0kob-small-Ep-838-SAVE-Act-SAVES-Ameri.jpg) LIVE
LIVE
The Nunn Report - w/ Dan Nunn
2 hours ago[Ep 838] SAVE Act SAVES America – Nuke Filibuster! | Dems Rage Baiting BS | Zohran Policies Kill 16
185 watching -
 7:00
7:00
Rethinking the Dollar
6 hours agoThe Silver Squeeze Just Got Real. Here’s What’s Coming!
13.4K4